[Last uptime 2020-12-25]
I need to run some ansible playbooks to a running (live) machine.
But, of-course, I cant use a production server for testing purposes !!
So here comes docker!
I have ssh access from my docker-server to this production server:
ssh livebox tar --one-file-system --sparse -C / -cf - | docker import - centos6:livebox on ubuntu 20.04
ssh livebox sudo tar -cf - --sparse --one-file-system / | docker import - centos6:livebox
Then run the new docker image:
$ docker run -t -i --rm -p 2222:22 centos6:livebox bash
[root@40b2bab2f306 /]# /usr/sbin/sshd -D
Create a new entry on your hosts inventory file, that uses ssh port 2222
or create a new separated inventory file
and test it with ansible ping module:
# ansible -m ping -i hosts.docker dockerlivebox
dockerlivebox | success >> {
"changed": false,
"ping": "pong"
}
Recently, I had the opportunity to see a presentation on the subject by Alexandros Kosiaris.
I was never fan of vagrant (or even virtualbox) but I gave it a try and below are my personal notes on the matter.
All my notes are based on Archlinux as it is my primary distribution but I think you can try them with every Gnu Linux OS.
Vagrant
So what is Vagrant ?
Vagrant is a wrapper, an abstraction layer to deal with some virtual solutions, like virtualbox, Vmware, hyper-v, docker, aws etc etc etc
With a few lines you can describe what you want to do and then use vagrant to create your enviroment of virtual boxes to work with.
Just for the fun of it, I used docker
Docker
We first need to create and build a proper Docker Image!
The Dockerfile below, is suggesting that we already have an archlinux:latest docker image.
You can use your own dockerfile or docker image.
You need to have an ssh connection to this docker image and you will need -of course- to have a ssh password or a ssh authorized key built in this image for root. If you are using sudo (then even better) dont forget to add the user to sudoers!
# vim Dockerfile
# sshd on archlinux
#
# VERSION 0.0.2
FROM archlinux:latest
MAINTAINER Evaggelos Balaskas < evaggelos _AT_ balaskas _DOT_ gr >
# Update the repositories
RUN pacman -Syy && pacman -S --noconfirm openssh python2
# Generate host keys
RUN /usr/bin/ssh-keygen -A
# Add password to root user
RUN echo 'root:roottoor' | chpasswd
# Fix sshd
RUN sed -i -e 's/^UsePAM yes/UsePAM no/g' /etc/ssh/sshd_config && echo 'PermitRootLogin yes' >> /etc/ssh/sshd_config
# Expose tcp port
EXPOSE 22
# Run openssh daemon
CMD ["/usr/sbin/sshd", "-D"]
Again, you dont need to follow this step by the book!
It is an example to understand that you need a proper docker image that you can ssh into it.
Build the docker image:
# docker build -t archlinux:sshd .
On my PC:
# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
archlinux sshd 1b074ffe98be 7 days ago 636.2 MB
archlinux latest c0c56d24b865 7 days ago 534 MB
archlinux devel e66b5b8af509 2 weeks ago 607 MB
centos6 powerdns daf76074f848 3 months ago 893 MB
centos6 newdnsps 642462a8dfb4 3 months ago 546.6 MB
centos7 cloudstack b5e696e65c50 6 months ago 1.463 GB
centos7 latest d96affc2f996 6 months ago 500.2 MB
centos6 latest 4ba27f5a1189 6 months ago 489.8 MB
Environment
We can define docker as our default provider with:
# export VAGRANT_DEFAULT_PROVIDER=docker
It is not necessary to define the default provider, as you will see below,
but it is also a good idea - if your forget to declare your vagrant provider later
Before we start with vagrant, let us create a new folder:
# mkdir -pv vagrant
# cd vagrant
Initialization
We are ready to initialized our enviroment for vagrant:
# vagrant init
A `Vagrantfile` has been placed in this directory. You are now
ready to `vagrant up` your first virtual environment! Please read
the comments in the Vagrantfile as well as documentation on
`vagrantup.com` for more information on using Vagrant.
Initial Vagrantfile
A typical vagrant configuration file looks something like this:
# cat Vagrantfile
cat Vagrantfile
# -*- mode: ruby -*-
# vi: set ft=ruby :
# All Vagrant configuration is done below. The "2" in Vagrant.configure
# configures the configuration version (we support older styles for
# backwards compatibility). Please don't change it unless you know what
# you're doing.
Vagrant.configure("2") do |config|
# The most common configuration options are documented and commented below.
# For a complete reference, please see the online documentation at
# https://docs.vagrantup.com.
# Every Vagrant development environment requires a box. You can search for
# boxes at https://atlas.hashicorp.com/search.
config.vm.box = "base"
# Disable automatic box update checking. If you disable this, then
# boxes will only be checked for updates when the user runs
# `vagrant box outdated`. This is not recommended.
# config.vm.box_check_update = false
# Create a forwarded port mapping which allows access to a specific port
# within the machine from a port on the host machine. In the example below,
# accessing "localhost:8080" will access port 80 on the guest machine.
# config.vm.network "forwarded_port", guest: 80, host: 8080
# Create a private network, which allows host-only access to the machine
# using a specific IP.
# config.vm.network "private_network", ip: "192.168.33.10"
# Create a public network, which generally matched to bridged network.
# Bridged networks make the machine appear as another physical device on
# your network.
# config.vm.network "public_network"
# Share an additional folder to the guest VM. The first argument is
# the path on the host to the actual folder. The second argument is
# the path on the guest to mount the folder. And the optional third
# argument is a set of non-required options.
# config.vm.synced_folder "../data", "/vagrant_data"
# Provider-specific configuration so you can fine-tune various
# backing providers for Vagrant. These expose provider-specific options.
# Example for VirtualBox:
#
# config.vm.provider "virtualbox" do |vb|
# # Display the VirtualBox GUI when booting the machine
# vb.gui = true
#
# # Customize the amount of memory on the VM:
# vb.memory = "1024"
# end
#
# View the documentation for the provider you are using for more
# information on available options.
# Define a Vagrant Push strategy for pushing to Atlas. Other push strategies
# such as FTP and Heroku are also available. See the documentation at
# https://docs.vagrantup.com/v2/push/atlas.html for more information.
# config.push.define "atlas" do |push|
# push.app = "YOUR_ATLAS_USERNAME/YOUR_APPLICATION_NAME"
# end
# Enable provisioning with a shell script. Additional provisioners such as
# Puppet, Chef, Ansible, Salt, and Docker are also available. Please see the
# documentation for more information about their specific syntax and use.
# config.vm.provision "shell", inline: <<-SHELL
# apt-get update
# apt-get install -y apache2
# SHELL
end
If you try to run this Vagrant configuration file with docker provider,
it will try to boot up base image (Vagrant Default box):
# vagrant up --provider=docker
Bringing machine 'default' up with 'docker' provider...
==> default: Box 'base' could not be found. Attempting to find and install...
default: Box Provider: docker
default: Box Version: >= 0
==> default: Box file was not detected as metadata. Adding it directly...
==> default: Adding box 'base' (v0) for provider: docker
default: Downloading: base
An error occurred while downloading the remote file. The error
message, if any, is reproduced below. Please fix this error and try
again.
Couldn't open file /ebal/Desktop/vagrant/base
Vagrantfile
Put the initial vagrantfile aside and create the below Vagrant configuration file:
Vagrant.configure("2") do |config|
config.vm.provider "docker" do |d|
d.image = "archlinux:sshd"
end
end
That translate to :
Vagrant Provider: docker
Docker Image: archlinux:sshd
Basic commands
Run vagrant to create our virtual box:
# vagrant up
Bringing machine 'default' up with 'docker' provider...
==> default: Creating the container...
default: Name: vagrant_default_1466368592
default: Image: archlinux:sshd
default: Volume: /home/ebal/Desktop/vagrant:/vagrant
default:
default: Container created: 4cf4649b47615469
==> default: Starting container...
==> default: Provisioners will not be run since container doesn't support SSH.
ok, we havent yet configured vagrant to use ssh
but we have a running docker instance:
# vagrant status
Current machine states:
default running (docker)
The container is created and running. You can stop it using
`vagrant halt`, see logs with `vagrant docker-logs`, and
kill/destroy it with `vagrant destroy`.
that we can verify with docker ps:
# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
4cf4649b4761 archlinux:sshd "/usr/sbin/sshd -D" About a minute ago Up About a minute 22/tcp vagrant_default_1466368592
Destroy
We need to destroy this instance:
# vagrant destroy
default: Are you sure you want to destroy the 'default' VM? [y/N] y
==> default: Stopping container...
==> default: Deleting the container...
Vagrant ssh
We need to edit Vagrantfile to add ssh support to our docker :
# vim Vagrantfile
Vagrant.configure("2") do |config|
config.vm.provider "docker" do |d|
d.image = "archlinux:sshd"
d.has_ssh = true
end
end
and re-up our vagrant box:
# vagrant up
Bringing machine 'default' up with 'docker' provider...
==> default: Creating the container...
default: Name: vagrant_default_1466368917
default: Image: archlinux:sshd
default: Volume: /home/ebal/Desktop/vagrant:/vagrant
default: Port: 127.0.0.1:2222:22
default:
default: Container created: b4fce563a9f9042c
==> default: Starting container...
==> default: Waiting for machine to boot. This may take a few minutes...
default: SSH address: 172.17.0.2:22
default: SSH username: vagrant
default: SSH auth method: private key
default: Warning: Authentication failure. Retrying...
default: Warning: Authentication failure. Retrying...
Vagrant will try to connect to our docker instance with the user: vagrant and a key.
But our docker image only have a root user and a root password !!
# vagrant status
Current machine states:
default running (docker)
The container is created and running. You can stop it using
`vagrant halt`, see logs with `vagrant docker-logs`, and
kill/destroy it with `vagrant destroy`.
# vagrant destroy
default: Are you sure you want to destroy the 'default' VM? [y/N] y
==> default: Stopping container...
==> default: Deleting the container...
Vagrant ssh - the Correct way !
We need to edit the Vagrantfile, properly:
# vim Vagrantfile
Vagrant.configure("2") do |config|
config.ssh.username = 'root'
config.ssh.password = 'roottoor'
config.vm.provider "docker" do |d|
d.image = "archlinux:sshd"
d.has_ssh = true
end
end
# vagrant up
Bringing machine 'default' up with 'docker' provider...
==> default: Creating the container...
default: Name: vagrant_default_1466369126
default: Image: archlinux:sshd
default: Volume: /home/ebal/Desktop/vagrant:/vagrant
default: Port: 127.0.0.1:2222:22
default:
default: Container created: 7fef0efc8905bb3a
==> default: Starting container...
==> default: Waiting for machine to boot. This may take a few minutes...
default: SSH address: 172.17.0.2:22
default: SSH username: root
default: SSH auth method: password
default: Warning: Connection refused. Retrying...
default:
default: Inserting generated public key within guest...
default: Removing insecure key from the guest if it's present...
default: Key inserted! Disconnecting and reconnecting using new SSH key...
==> default: Machine booted and ready!
# vagrant status
Current machine states:
default running (docker)
The container is created and running. You can stop it using
`vagrant halt`, see logs with `vagrant docker-logs`, and
kill/destroy it with `vagrant destroy`.
# vagrant ssh-config
Host default
HostName 172.17.0.2
User root
Port 22
UserKnownHostsFile /dev/null
StrictHostKeyChecking no
PasswordAuthentication no
IdentityFile /tmp/vagrant/.vagrant/machines/default/docker/private_key
IdentitiesOnly yes
LogLevel FATAL
# vagrant ssh
[root@7fef0efc8905 ~]# uptime
20:45:48 up 11:33, 0 users, load average: 0.53, 0.42, 0.28
[root@7fef0efc8905 ~]#
[root@7fef0efc8905 ~]#
[root@7fef0efc8905 ~]#
[root@7fef0efc8905 ~]# exit
logout
Connection to 172.17.0.2 closed.
Ansible
It is time to add ansible to the mix!
Ansible Playbook
We need to create a basic ansible playbook:
# cat playbook.yml
---
- hosts: all
vars:
ansible_python_interpreter: "/usr/bin/env python2"
gather_facts: no
tasks:
# Install package vim
- pacman: name=vim state=present
The above playbook, is going to install vim, via pacman (archlinux PACkage MANager)!
Archlinux comes by default with python3 and with ansible_python_interpreter you are declaring to use python2!
Vagrantfile with Ansible
# cat Vagrantfile
Vagrant.configure("2") do |config|
config.ssh.username = 'root'
config.ssh.password = 'roottoor'
config.vm.provider "docker" do |d|
d.image = "archlinux:sshd"
d.has_ssh = true
end
config.vm.provision "ansible" do |ansible|
ansible.verbose = "v"
ansible.playbook = "playbook.yml"
end
end
Vagrant Docker Ansible
# vagrant up
Bringing machine 'default' up with 'docker' provider...
==> default: Creating the container...
default: Name: vagrant_default_1466370194
default: Image: archlinux:sshd
default: Volume: /home/ebal/Desktop/vagrant:/vagrant
default: Port: 127.0.0.1:2222:22
default:
default: Container created: 8909eee7007b8d4f
==> default: Starting container...
==> default: Waiting for machine to boot. This may take a few minutes...
default: SSH address: 172.17.0.2:22
default: SSH username: root
default: SSH auth method: password
default: Warning: Connection refused. Retrying...
default:
default: Inserting generated public key within guest...
default: Removing insecure key from the guest if it's present...
default: Key inserted! Disconnecting and reconnecting using new SSH key...
==> default: Machine booted and ready!
==> default: Running provisioner: ansible...
default: Running ansible-playbook...
PYTHONUNBUFFERED=1 ANSIBLE_FORCE_COLOR=true ANSIBLE_HOST_KEY_CHECKING=false ANSIBLE_SSH_ARGS='-o UserKnownHostsFile=/dev/null -o IdentitiesOnly=yes -o ControlMaster=auto -o ControlPersist=60s' ansible-playbook --connection=ssh --timeout=30 --limit="default" --inventory-file=/mnt/VB0250EAVER/home/ebal/Desktop/vagrant/.vagrant/provisioners/ansible/inventory -v playbook.yml
Using /etc/ansible/ansible.cfg as config file
PLAY [all] *********************************************************************
TASK [pacman] ******************************************************************
changed: [default] => {"changed": true, "msg": "installed 1 package(s). "}
PLAY RECAP *********************************************************************
default : ok=1 changed=1 unreachable=0 failed=0
# vagrant status
Current machine states:
default running (docker)
The container is created and running. You can stop it using
`vagrant halt`, see logs with `vagrant docker-logs`, and
kill/destroy it with `vagrant destroy`.
# vagrant ssh
[root@8909eee7007b ~]# vim --version
VIM - Vi IMproved 7.4 (2013 Aug 10, compiled Jun 9 2016 09:35:16)
Included patches: 1-1910
Compiled by Arch Linux
Vagrant Provisioning
The ansible-step is called: provisioning as you may already noticed.
If you make a few changes on this playbook, just type:
# vagrant provision
and it will re-run the ansible part on this vagrant box !
Personal Notes on this blog post.
[work in progress]
Why ?
Γιατί docker ?
To docker είναι ένα management εργαλείο για διαχείριση containers.
Εάν κι αρχικά βασίστηκε σε lxc, πλέον είναι αυτοτελές.
Containers είναι ένα isolated περιβάλλον, κάτι περισσότερο από
chroot(jail) κάτι λιγότερο από virtual machines.
Μπορούμε να σηκώσουμε αρκετά linux λειτουργικά, αλλά της ίδιας αρχιτεκτονικής.
Χρησιμοποιούνται κυρίως για development αλλά πλέον τρέχει μεγάλη
production υποδομή σε μεγάλα projects.
Κερδίζει γιατί το docker image που έχω στο PC μου, μπορεί να τρέξει αυτούσιο
σε οποιοδήποτε linux λειτουργικό (centos/fedora/debian/archlinux/whatever)
και προσφέρει isolation μεταξύ της εφαρμογής που τρέχει και του λειτουργικού.
Οι επιδόσεις -πλέον- είναι πολύ κοντά σε αυτές του συστήματος.
Σε production κυρίως χρησιμοποιείτε για continuous deployment,
καθώς τα images μπορεί να τα παράγουν developers, vendors ή whatever,
και θα παίξει σε commodity server με οποιοδήποτε λειτουργικό σύστημα!
Οπότε πλέον το “Σε εμένα παίζει” με το docker μεταφράζεται σε
“Και σε εμένα παίζει” !! στην παραγωγή.
Info
Εάν δεν τρέχει το docker:
# systemctl restart docker
basic info on CentOS7 με devicemapper
# docker info
Containers: 0
Images: 4
Server Version: 1.9.1
Storage Driver: devicemapper
Pool Name: docker-8:1-10617750-pool
Pool Blocksize: 65.54 kB
Base Device Size: 107.4 GB
Backing Filesystem:
Data file: /dev/loop0
Metadata file: /dev/loop1
Data Space Used: 1.654 GB
Data Space Total: 107.4 GB
Data Space Available: 105.7 GB
Metadata Space Used: 1.642 MB
Metadata Space Total: 2.147 GB
Metadata Space Available: 2.146 GB
Udev Sync Supported: true
Deferred Removal Enabled: false
Deferred Deletion Enabled: false
Deferred Deleted Device Count: 0
Data loop file: /var/lib/docker/devicemapper/devicemapper/data
Metadata loop file: /var/lib/docker/devicemapper/devicemapper/metadata
Library Version: 1.02.107-RHEL7 (2015-12-01)
Execution Driver: native-0.2
Logging Driver: json-file
Kernel Version: 3.10.0-327.13.1.el7.x86_64
Operating System: CentOS Linux 7 (Core)
CPUs: 16
Total Memory: 15.66 GiB
Name: myserverpc
ID: DCO7:RO56:3EWH:ESM3:257C:TCA3:JPLD:QFLU:EHKL:QXKU:GJYI:SHY5
basic info σε archlinux με btrfs :
# docker info
Containers: 0
Running: 0
Paused: 0
Stopped: 0
Images: 8
Server Version: 1.11.1
Storage Driver: btrfs
Build Version: Btrfs v4.5.1
Library Version: 101
Logging Driver: json-file
Cgroup Driver: cgroupfs
Plugins:
Volume: local
Network: null host bridge
Kernel Version: 4.4.11-1-lts
Operating System: Arch Linux
OSType: linux
Architecture: x86_64
CPUs: 4
Total Memory: 7.68 GiB
Name: myhomepc
ID: MSCX:LLTD:YKZS:E7UN:NIA4:QW3F:SRGC:RQTH:RKE2:26VS:GFB5:Y7CS
Docker Root Dir: /var/lib/docker/
Debug mode (client): false
Debug mode (server): false
Registry: https://index.docker.io/v1/
Images
# docker images -a
REPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZE
centos6 rpmbuild ccb144691075 11 days ago 1.092 GB
< none > < none > 6d8ff86f2749 11 days ago 1.092 GB
< none > < none > af92904a92b4 11 days ago 811.8 MB
< none > < none > 8e429b38312b 11 days ago 392.7 MB
Τα none:none είναι built parent images που χρησιμοποιούνται από τα named docker images
αλλά δεν τα αποθηκεύσαμε σωστά.
Understanding Images
Ανάλογα με το back-end του docker, το docker κρατά σε delta-layers τις διαφορές
ανάμεσα στα parent/child docker images.
Αυτό μας διευκολύνει, γιατί μπορούμε στο production να έχουμε μεγάλες μήτρες από docker images
και να στέλνουμε μικρά delta-child docker images με το production service που θέλουμε να τρέξουμε.
Επίσης βοηθά και στο update.
Σε έξι μήνες, από την αρχική μας εικόνα, φτιάχνουμε το update image και πάνω σε αυτό
ξαναφορτώνουμε την εφαρμογή ή service που θέλουμε να τρέξει.
Έτσι μπορούμε να στέλνουμε μικρά σε μέγεθος docker images και να γίνονται build
τα διάφορα services μας πάνω σε αυτά.
Στο myserverpc μέσω του docker info είδαμε πως τρέχει σε:
Storage Driver: devicemapper
και χρησιμοποιεί το παρακάτω αρχείο για να κρατά τα images :
Data loop file: /var/lib/docker/devicemapper/devicemapper/data
Το οποίο στην πραγματικότητα είναι:
# file data
data: SGI XFS filesystem data (blksz 4096, inosz 256, v2 dirs)
Τα πιο δημοφιλή storage drivers είναι τα UFS & btrfs.
Προσωπικά (ebal) χρησιμοποιώ btrfs γιατί χρησιμοποιεί subvolumes
(σαν να λέμε ξεχωριστά cow volumes) για κάθε docker image
(parent ή child).
# ls /var/lib/docker/btrfs/subvolumes
070dd70b48c86828463a7341609a7ee4924decd4d7fdd527e9fbaa70f7a0caf8
1fb7e53272a8f01801d9e413c823cbb8cbc83bfe1218436bdb9e658ea2e8b755
632cceadcc05f28dda37b39b8a9111bb004a9bdaeca59c0300196863ee44ad0a
8bfbbf03c00863bc19f46aa994d1458c0b5454529ad6af1203fb6e2599a35e91
93bb08f5730368de14719109142232249dc6b3a0571a0157b2a043d7fc94117a
a174a1b850ae50dfaf1c13ede7fe37cc0cb574498a2faa4b0e80a49194d0e115
d0e92b9a33b207c679e8a05da56ef3bf9a750bddb124955291967e0af33336fc
e9904ddda15030a210c7d741701cca55a44b89fd320e2253cfcb6e4a3f905669
Processes
Τι docker process τρέχουν:
# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
ενώ όταν τρέχει κάποιο:
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
62ef0ed8bc95 centos6:rpmbuild "bash" 10 seconds ago Up 9 seconds drunk_mietner
Δώστε σημασία στο NAMES
To docker δίνει randomly δύο ονόματα για ευκολότερη διαχείριση,
αλλιώς θα πρέπει να χρησιμοποιούμε το πλήρες hashed named.
Στο παραπάνω παράδειγμα:
62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f
Inspect
Πως παίρνουμε πληροφορίες από ένα docker process:
# docker inspect drunk_mietner
[
{
"Id": "62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f",
"Created": "2016-06-05T07:41:18.821123985Z",
"Path": "bash",
"Args": [],
"State": {
"Status": "running",
"Running": true,
"Paused": false,
"Restarting": false,
"OOMKilled": false,
"Dead": false,
"Pid": 23664,
"ExitCode": 0,
"Error": "",
"StartedAt": "2016-06-05T07:41:19.558616976Z",
"FinishedAt": "0001-01-01T00:00:00Z"
},
"Image": "ccb1446910754d6572976a6d36e5d0c8d1d029e4dc72133211670b28cf2f1d8f",
"ResolvConfPath": "/var/lib/docker/containers/62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f/resolv.conf",
"HostnamePath": "/var/lib/docker/containers/62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f/hostname",
"HostsPath": "/var/lib/docker/containers/62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f/hosts",
"LogPath": "/var/lib/docker/containers/62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f/62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f-json.log",
"Name": "/drunk_mietner",
"RestartCount": 0,
"Driver": "devicemapper",
"ExecDriver": "native-0.2",
"MountLabel": "system_u:object_r:svirt_sandbox_file_t:s0:c344,c750",
"ProcessLabel": "system_u:system_r:svirt_lxc_net_t:s0:c344,c750",
"AppArmorProfile": "",
"ExecIDs": null,
"HostConfig": {
"Binds": null,
"ContainerIDFile": "",
"LxcConf": [],
"Memory": 0,
"MemoryReservation": 0,
"MemorySwap": 0,
"KernelMemory": 0,
"CpuShares": 0,
"CpuPeriod": 0,
"CpusetCpus": "",
"CpusetMems": "",
"CpuQuota": 0,
"BlkioWeight": 0,
"OomKillDisable": false,
"MemorySwappiness": -1,
"Privileged": false,
"PortBindings": {},
"Links": null,
"PublishAllPorts": false,
"Dns": [],
"DnsOptions": [],
"DnsSearch": [],
"ExtraHosts": null,
"VolumesFrom": null,
"Devices": [],
"NetworkMode": "default",
"IpcMode": "",
"PidMode": "",
"UTSMode": "",
"CapAdd": null,
"CapDrop": null,
"GroupAdd": null,
"RestartPolicy": {
"Name": "no",
"MaximumRetryCount": 0
},
"SecurityOpt": null,
"ReadonlyRootfs": false,
"Ulimits": null,
"Sysctls": {},
"LogConfig": {
"Type": "json-file",
"Config": {}
},
"CgroupParent": "",
"ConsoleSize": [
0,
0
],
"VolumeDriver": "",
"ShmSize": 67108864
},
"GraphDriver": {
"Name": "devicemapper",
"Data": {
"DeviceId": "13",
"DeviceName": "docker-8:1-10617750-62ef0ed8bc952d501f241dbc4ecda25d3a629880d27fbb7344b5429a44af985f",
"DeviceSize": "107374182400"
}
},
"Mounts": [],
"Config": {
"Hostname": "62ef0ed8bc95",
"Domainname": "",
"User": "",
"AttachStdin": true,
"AttachStdout": true,
"AttachStderr": true,
"Tty": true,
"OpenStdin": true,
"StdinOnce": true,
"Env": null,
"Cmd": [
"bash"
],
"Image": "centos6:rpmbuild",
"Volumes": null,
"WorkingDir": "",
"Entrypoint": null,
"OnBuild": null,
"Labels": {},
"StopSignal": "SIGTERM"
},
"NetworkSettings": {
"Bridge": "",
"SandboxID": "992cf9db43c309484b8261904f46915a15eff3190026749841b93072847a14bc",
"HairpinMode": false,
"LinkLocalIPv6Address": "",
"LinkLocalIPv6PrefixLen": 0,
"Ports": {},
"SandboxKey": "/var/run/docker/netns/992cf9db43c3",
"SecondaryIPAddresses": null,
"SecondaryIPv6Addresses": null,
"EndpointID": "17b09b362d3b2be7d9c48377969049ac07cb821c482a9644970567fd5bb772f1",
"Gateway": "172.17.0.1",
"GlobalIPv6Address": "",
"GlobalIPv6PrefixLen": 0,
"IPAddress": "172.17.0.2",
"IPPrefixLen": 16,
"IPv6Gateway": "",
"MacAddress": "02:42:ac:11:00:02",
"Networks": {
"bridge": {
"EndpointID": "17b09b362d3b2be7d9c48377969049ac07cb821c482a9644970567fd5bb772f1",
"Gateway": "172.17.0.1",
"IPAddress": "172.17.0.2",
"IPPrefixLen": 16,
"IPv6Gateway": "",
"GlobalIPv6Address": "",
"GlobalIPv6PrefixLen": 0,
"MacAddress": "02:42:ac:11:00:02"
}
}
}
}
]
output σε json, που σημαίνει εύκολο provisioning !!!
Import
Ο πιο εύκολος τρόπος είναι να έχουμε ένα tar archive
από το σύστημα που θέλουμε και να το κάνουμε import:
# docker import - centos6:latest < a.tar
Run
Πως σηκώνουμε ένα docker image:
# docker run -t -i --rm centos6:latest bash
Αυτό σημαίνει πως θα μας δώσει interactive process με entry-point το bash.
Τέλος, μόλις κλείσουμε το docker image θα εξαφανιστούν ΟΛΕΣ οι αλλαγές που έχουμε κάνει.
Χρειάζεται να τα διαγράφουμε, για να μην γεμίσουμε με images που έχουν μεταξύ τους μικρές αλλαγές
Μπορούμε να έχουμε docker processes χωρίς entry-point.
Αυτά είναι τα service oriented containers που το entry-point
είναι TCP port (συνήθως) και τρέχουν τα διάφορα services που θέλουμε.
Όλα αυτά αργότερα.
Inside
Μέσα σε ένα docker image:
[root@62ef0ed8bc95 /]# hostname
62ef0ed8bc95
# ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
11: eth0@if12: mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::42:acff:fe11:2/64 scope link
valid_lft forever preferred_lft forever
# ip r
default via 172.17.0.1 dev eth0
172.17.0.0/16 dev eth0 proto kernel scope link src 172.17.0.2
private network 172.x.x.x
το οποίο έχει δημιουργηθεί από το myserverpc:
10: docker0: mtu 1500 qdisc noqueue state UP
link/ether 02:42:24:5c:42:f6 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:24ff:fe5c:42f6/64 scope link
valid_lft forever preferred_lft forever
12: veth524ea1d@if11: mtu 1500 qdisc noqueue master docker0 state UP
link/ether 6e:39:ae:aa:ec:65 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet6 fe80::6c39:aeff:feaa:ec65/64 scope link
valid_lft forever preferred_lft forever
# brctl show
bridge name bridge id STP enabled interfaces
docker0 8000.0242245c42f6 no veth524ea1d
virbr0 8000.525400990c9d yes virbr0-nic
Commit
ok, έχουμε κάνει τις αλλαγές μας ή έχουμε στήσει μια μήτρα ενός docker image
που θέλουμε να κρατήσουμε. Πως το κάνουμε commit ?
Από το myserverpc (κι όχι μέσα από το docker process):
# docker commit -p -m "centos6 rpmbuild test image" drunk_mietner centos6:rpmbuildtest
Το βλέπουμε πως έχει δημιουργηθεί:
# docker images
REPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZE
centos6 rpmbuildtest 95246c3b7b8b 3 seconds ago 1.092 GB
centos6 rpmbuild ccb144691075 11 days ago 1.092 GB
Remove
και δεν το χρειαζόμαστε πλέον, θέλουμε να κρατήσουμε μόνο το centos6:rpmbuild
Εάν δεν έχει child docker images και δεν τρέχει κάποιο docker process βασισμένο σε αυτό το docker:
# docker rmi centos6:rpmbuildtest
Untagged: centos6:rpmbuildtest
Deleted: 95246c3b7b8b77e9f5c70f2fd7b8ea2c8ec1f72e846897c87cd60722f6caabef
# docker images
REPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZE
centos6 rpmbuild ccb144691075 11 days ago 1.092 GB
< none > < none > 6d8ff86f2749 11 days ago 1.092 GB
Export
οκ, έχουμε φτιάξει στον υπολογιστή μας το τέλειο docker image
και θέλουμε να το κάνουμε export για να το φορτώσουμε κάπου αλλού:
# docker export drunk_mietner > CentOS68_rpmbuild.tar
These are my personal notes on upgrading wallabag to it’s latest version (2.0.8):
Create a backup
# cd /var/www/html/
# mv wallabag wallabag_bak
Download latest version
# wget -c http://wllbg.org/latest-v2-package -qO - | tar -xz
# mv release-2.0.8 wallabag
Restore Settings
# cp -f wallabag_bak/app/config/parameters.yml wallabag/app/config/parameters.yml
# rsync -r wallabag_bak/data/ wallabag/data/
[h3] Permissions [h3]
Don’t forget to fix the permissions on wallabag according to your web server settings:
# chown -R apache:apache wallabag
and …. that’s it !
Let’s Encrypt client: certbot is been written in python and as it’s predecessor needs at least Python 2.7.
But (still) in CentOS series 6 (currently 6.8) there is no natively support for python27.
So I did this thing below, quick & dirty:
# cd /usr/local/src/
# wget -c https://www.python.org/ftp/python/2.7.11/Python-2.7.11.tgz
# tar xf Python-2.7.11.tgz
# cd Python-2.7.11
# ./configure
# make
# make install
and these are my notes for renew certificates :
# ln -s /opt/Python-2.7/bin/python2.7 /usr/local/bin/python2
[root@1 certbot]# source venv/bin/activate
(venv)[root@1 certbot]#
# cd venv/bin/
# ./certbot renew --dry-run
# ./certbot renew
# rm /usr/local/bin/python2
Domain-based Message Authentication, Reporting and Conformance
What is dmarc in a nutshell:
An authentication Protocol that combines SPF & DKIM to reduce spoofed emails.
Depends on DNS so DANE would be great here!
notes on centos6:
You need to already have implemented SPF & DKIM
Outgoing Mail Servers
DNS
in your zone file, add something like this:
_dmarc IN TXT "v=DMARC1; p=none; rua=mailto:postmaster@example.org"
increase the serial number of the zone and check it:
# dig +short txt _dmarc.example.org
"v=DMARC1; p=none; rua=mailto:postmaster@example.org"
dmarc tags
DMARC requires only two tags.
v: version
p: policy
version
Version is DMARC1 for the time being
policy
p=none
p=quarantine
p=reject
We start from policy=none and trying to investigate mail logs
reports
rua declares where the mail servers will send the reports regarding dmarc failures.
Incoming Mail Servers
installation
# yum search opendmarc
# yum -y install opendmarc.x86_64
check process:
# netstat -ntlp|grep dmarc
tcp 0 0 127.0.0.1:8893 0.0.0.0:* LISTEN 14538/opendmarc
postfix
Add another milter:
# opendkim & opendmarc
non_smtpd_milters=inet:127.0.0.1:8891,inet:127.0.0.1:8893
smtpd_milters=inet:127.0.0.1:8891,inet:127.0.0.1:8893
configuration
# grep -Ev '#|^$' /etc/opendmarc.conf
Socket inet:8893@localhost
SoftwareHeader true
SPFIgnoreResults true
SPFSelfValidate true
Syslog true
UMask 007
UserID opendmarc:mail
AuthservID example.org
MilterDebug 1
service
# /etc/init.d/opendmarc restart
# chkconfig opendmarc on
DMARC Inspector
The last couple months, I get over 400 unknown user errors on my imap (dovecot) server.
FYI this is the report:
dovecot: auth: ldap(aaaaaa,193.189.117.147): unknown user:
dovecot: auth: ldap(accountant,193.189.117.147): unknown user:
dovecot: auth: ldap(acosta,193.189.117.147): unknown user:
dovecot: auth: ldap(admin@balaskas.gr,89.248.162.175): unknown user:
dovecot: auth: ldap(adrian,193.189.117.152): unknown user:
dovecot: auth: ldap(alarm,193.189.117.152): unknown user:
dovecot: auth: ldap(alcala,185.125.4.192): unknown user:
dovecot: auth: ldap(alena,193.189.117.148): unknown user:
dovecot: auth: ldap(alfaro,185.125.4.192): unknown user:
dovecot: auth: ldap(alias,193.189.117.152): unknown user:
dovecot: auth: ldap(ally,185.125.4.192): unknown user:
dovecot: auth: ldap(almeida,185.125.4.192): unknown user:
dovecot: auth: ldap(alya,185.125.4.192): unknown user:
dovecot: auth: ldap(amara,185.125.4.192): unknown user:
dovecot: auth: ldap(amigo,185.125.4.192): unknown user:
dovecot: auth: ldap(amina,185.125.4.192): unknown user:
dovecot: auth: ldap(amity,185.125.4.192): unknown user:
dovecot: auth: ldap(analysis,185.125.4.192): unknown user:
dovecot: auth: ldap(analyst,185.125.4.192): unknown user:
dovecot: auth: ldap(anderson,185.125.4.192): unknown user:
dovecot: auth: ldap(andrade,185.125.4.192): unknown user:
dovecot: auth: ldap(andreea,185.125.4.192): unknown user:
dovecot: auth: ldap(andria,185.125.4.192): unknown user:
dovecot: auth: ldap(annalisa,185.125.4.192): unknown user:
dovecot: auth: ldap(annika,193.189.117.148): unknown user:
dovecot: auth: ldap(anon,185.125.4.192): unknown user:
dovecot: auth: ldap(anonymous,193.189.117.148): unknown user:
dovecot: auth: ldap(area,185.125.4.192): unknown user:
dovecot: auth: ldap(aris,185.125.4.192): unknown user:
dovecot: auth: ldap(arriaga,185.125.4.192): unknown user:
dovecot: auth: ldap(ashley,185.125.4.192): unknown user:
dovecot: auth: ldap(assistance,185.125.4.192): unknown user:
dovecot: auth: ldap(aya,185.125.4.192): unknown user:
dovecot: auth: ldap(azerty,185.125.4.192): unknown user:
dovecot: auth: ldap(baby,185.125.4.192): unknown user:
dovecot: auth: ldap(bad,185.125.4.192): unknown user:
dovecot: auth: ldap(ballesteros,185.125.4.192): unknown user:
dovecot: auth: ldap(banana,193.189.117.147): unknown user:
dovecot: auth: ldap(band,185.125.4.192): unknown user:
dovecot: auth: ldap(bank,193.189.117.149): unknown user:
dovecot: auth: ldap(barbara,193.189.117.147): unknown user:
dovecot: auth: ldap(barcode,193.189.117.147): unknown user:
dovecot: auth: ldap(barney,185.125.4.192): unknown user:
dovecot: auth: ldap(barrie,185.125.4.192): unknown user:
dovecot: auth: ldap(basil,185.125.4.192): unknown user:
dovecot: auth: ldap(bob,193.189.117.148): unknown user:
dovecot: auth: ldap(camp,155.133.82.65): unknown user:
dovecot: auth: ldap(campos,155.133.82.65): unknown user:
dovecot: auth: ldap(candi,155.133.82.65): unknown user:
dovecot: auth: ldap(carlo,193.189.117.147): unknown user:
dovecot: auth: ldap(carolina,193.189.117.147): unknown user:
dovecot: auth: ldap(cashier,193.189.117.148): unknown user:
dovecot: auth: ldap(casper,155.133.82.65): unknown user:
dovecot: auth: ldap(chad,155.133.82.65): unknown user:
dovecot: auth: ldap(challenge,155.133.82.65): unknown user:
dovecot: auth: ldap(chantal,155.133.82.65): unknown user:
dovecot: auth: ldap(charly,155.133.82.65): unknown user:
dovecot: auth: ldap(cher,155.133.82.65): unknown user:
dovecot: auth: ldap(cheryl,155.133.82.65): unknown user:
dovecot: auth: ldap(clare,155.133.82.65): unknown user:
dovecot: auth: ldap(classic,155.133.82.65): unknown user:
dovecot: auth: ldap(claudia,193.189.117.149): unknown user:
dovecot: auth: ldap(clock,155.133.82.65): unknown user:
dovecot: auth: ldap(consola,155.133.82.65): unknown user:
dovecot: auth: ldap(contactus,193.189.117.149): unknown user:
dovecot: auth: ldap(contract,155.133.82.65): unknown user:
dovecot: auth: ldap(craig,155.133.82.65): unknown user:
dovecot: auth: ldap(cuenta,155.133.82.65): unknown user:
dovecot: auth: ldap(cuentas,155.133.82.65): unknown user:
dovecot: auth: ldap(culture,155.133.82.65): unknown user:
dovecot: auth: ldap(dale,155.133.82.65): unknown user:
dovecot: auth: ldap(danielle,193.189.117.149): unknown user:
dovecot: auth: ldap(dante,155.133.82.65): unknown user:
dovecot: auth: ldap(davis,155.133.82.65): unknown user:
dovecot: auth: ldap(day,155.133.82.65): unknown user:
dovecot: auth: ldap(denis,193.189.117.149): unknown user:
dovecot: auth: ldap(dentrix,185.125.4.194): unknown user:
dovecot: auth: ldap(deposit,185.125.4.194): unknown user:
dovecot: auth: ldap(designer,185.125.4.194): unknown user:
dovecot: auth: ldap(desmond,155.133.82.65): unknown user:
dovecot: auth: ldap(devel,185.125.4.194): unknown user:
dovecot: auth: ldap(device,185.125.4.194): unknown user:
dovecot: auth: ldap(devin,185.125.4.194): unknown user:
dovecot: auth: ldap(diamante,185.125.4.194): unknown user:
dovecot: auth: ldap(digital,193.189.117.151): unknown user:
dovecot: auth: ldap(dimas,155.133.82.65): unknown user:
dovecot: auth: ldap(direktor,155.133.82.65): unknown user:
dovecot: auth: ldap(discount,185.125.4.194): unknown user:
dovecot: auth: ldap(discussion,185.125.4.194): unknown user:
dovecot: auth: ldap(disk,155.133.82.65): unknown user:
dovecot: auth: ldap(display,193.189.117.149): unknown user:
dovecot: auth: ldap(doctor,193.189.117.148): unknown user:
dovecot: auth: ldap(document,193.189.117.148): unknown user:
dovecot: auth: ldap(dolores,185.125.4.194): unknown user:
dovecot: auth: ldap(domingo,185.125.4.194): unknown user:
dovecot: auth: ldap(dominio,185.125.4.194): unknown user:
dovecot: auth: ldap(donald,185.125.4.194): unknown user:
dovecot: auth: ldap(donna,193.189.117.149): unknown user:
dovecot: auth: ldap(dorado,185.125.4.194): unknown user:
dovecot: auth: ldap(doreen,155.133.82.65): unknown user:
dovecot: auth: ldap(doris,155.133.82.65): unknown user:
dovecot: auth: ldap(dot,185.125.4.194): unknown user:
dovecot: auth: ldap(dovecot,193.189.117.151): unknown user:
dovecot: auth: ldap(draft,185.125.4.194): unknown user:
dovecot: auth: ldap(dragon,155.133.82.65): unknown user:
dovecot: auth: ldap(drama,155.133.82.65): unknown user:
dovecot: auth: ldap(drawing,185.125.4.194): unknown user:
dovecot: auth: ldap(dream,185.125.4.194): unknown user:
dovecot: auth: ldap(dundee,185.125.4.194): unknown user:
dovecot: auth: ldap(eagle,185.125.4.194): unknown user:
dovecot: auth: ldap(ear,185.125.4.194): unknown user:
dovecot: auth: ldap(easy,193.189.117.148): unknown user:
dovecot: auth: ldap(econom,185.125.4.194): unknown user:
dovecot: auth: ldap(eddy,185.125.4.194): unknown user:
dovecot: auth: ldap(edita,185.125.4.194): unknown user:
dovecot: auth: ldap(edu,185.125.4.194): unknown user:
dovecot: auth: ldap(education,193.189.117.151): unknown user:
dovecot: auth: ldap(eldon,185.125.4.194): unknown user:
dovecot: auth: ldap(elfa,185.125.4.194): unknown user:
dovecot: auth: ldap(eliza,185.125.4.194): unknown user:
dovecot: auth: ldap(elizabeth,193.189.117.151): unknown user:
dovecot: auth: ldap(ellen,185.125.4.194): unknown user:
dovecot: auth: ldap(elsie,185.125.4.194): unknown user:
dovecot: auth: ldap(elvin,185.125.4.194): unknown user:
dovecot: auth: ldap(emmanuel,193.189.117.151): unknown user:
dovecot: auth: ldap(empleos,193.189.117.149): unknown user:
dovecot: auth: ldap(enrique,193.189.117.151): unknown user:
dovecot: auth: ldap(envio,193.189.117.148): unknown user:
dovecot: auth: ldap(erin,193.189.117.151): unknown user:
dovecot: auth: ldap(estel,193.189.117.151): unknown user:
dovecot: auth: ldap(fax@balaskas.gr,212.67.127.105): unknown user:
dovecot: auth: ldap(felipe,193.189.117.149): unknown user:
dovecot: auth: ldap(fischer,193.189.117.151): unknown user:
dovecot: auth: ldap(florence,193.189.117.149): unknown user:
dovecot: auth: ldap(forum,193.189.117.148): unknown user:
dovecot: auth: ldap(fred,193.189.117.149): unknown user:
dovecot: auth: ldap(giuseppe,193.189.117.149): unknown user:
dovecot: auth: ldap(golden,193.189.117.151): unknown user:
dovecot: auth: ldap(hannah,193.189.117.149): unknown user:
dovecot: auth: ldap(henry,193.189.117.148): unknown user:
dovecot: auth: ldap(home,193.189.117.148): unknown user:
dovecot: auth: ldap(howard,193.189.117.151): unknown user:
dovecot: auth: ldap(hudson,193.189.117.149): unknown user:
dovecot: auth: ldap(ian,193.189.117.149): unknown user:
dovecot: auth: ldap(info@balaskas.gr,89.248.162.175): unknown user:
dovecot: auth: ldap(ingrid,193.189.117.151): unknown user:
dovecot: auth: ldap(inspector,193.189.117.151): unknown user:
dovecot: auth: ldap(installer,193.189.117.147): unknown user:
dovecot: auth: ldap(invite,193.189.117.149): unknown user:
dovecot: auth: ldap(irena,193.189.117.151): unknown user:
dovecot: auth: ldap(irene,193.189.117.147): unknown user:
dovecot: auth: ldap(isabel,193.189.117.151): unknown user:
dovecot: auth: ldap(ivan,193.189.117.148): unknown user:
dovecot: auth: ldap(jackie,193.189.117.149): unknown user:
dovecot: auth: ldap(jaime,193.189.117.151): unknown user:
dovecot: auth: ldap(jane,193.189.117.148): unknown user:
dovecot: auth: ldap(jerry,193.189.117.149): unknown user:
dovecot: auth: ldap(jo,193.189.117.151): unknown user:
dovecot: auth: ldap(joanna,193.189.117.148): unknown user:
dovecot: auth: ldap(joaquin,193.189.117.151): unknown user:
dovecot: auth: ldap(job,193.189.117.149): unknown user:
dovecot: auth: ldap(joline,185.125.4.196): unknown user:
dovecot: auth: ldap(jon,193.189.117.147): unknown user:
dovecot: auth: ldap(jose,193.189.117.147): unknown user:
dovecot: auth: ldap(joy,185.125.4.196): unknown user:
dovecot: auth: ldap(js,193.189.117.148): unknown user:
dovecot: auth: ldap(juanita,185.125.4.196): unknown user:
dovecot: auth: ldap(jule,185.125.4.196): unknown user:
dovecot: auth: ldap(julian,193.189.117.149): unknown user:
dovecot: auth: ldap(julieta,185.125.4.196): unknown user:
dovecot: auth: ldap(justin,193.189.117.147): unknown user:
dovecot: auth: ldap(kai,185.125.4.196): unknown user:
dovecot: auth: ldap(karan,185.125.4.196): unknown user:
dovecot: auth: ldap(karina,193.189.117.151): unknown user:
dovecot: auth: ldap(kathy,193.189.117.149): unknown user:
dovecot: auth: ldap(keith,193.189.117.149): unknown user:
dovecot: auth: ldap(keller,185.125.4.196): unknown user:
dovecot: auth: ldap(kelvin,185.125.4.196): unknown user:
dovecot: auth: ldap(kennedy,185.125.4.196): unknown user:
dovecot: auth: ldap(kernel,185.125.4.196): unknown user:
dovecot: auth: ldap(kid,185.125.4.196): unknown user:
dovecot: auth: ldap(kiki,193.189.117.149): unknown user:
dovecot: auth: ldap(kim,193.189.117.147): unknown user:
dovecot: auth: ldap(kimberley,185.125.4.196): unknown user:
dovecot: auth: ldap(kind,185.125.4.196): unknown user:
dovecot: auth: ldap(king,193.189.117.149): unknown user:
dovecot: auth: ldap(kiosk,193.189.117.147): unknown user:
dovecot: auth: ldap(kip,193.189.117.151): unknown user:
dovecot: auth: ldap(kira,193.189.117.151): unknown user:
dovecot: auth: ldap(kirk,185.125.4.196): unknown user:
dovecot: auth: ldap(kirsten,185.125.4.196): unknown user:
dovecot: auth: ldap(kitty,193.189.117.149): unknown user:
dovecot: auth: ldap(knife,185.125.4.196): unknown user:
dovecot: auth: ldap(koko,185.125.4.196): unknown user:
dovecot: auth: ldap(kraft,185.125.4.196): unknown user:
dovecot: auth: ldap(kris,185.125.4.196): unknown user:
dovecot: auth: ldap(kym,185.125.4.196): unknown user:
dovecot: auth: ldap(kyra,185.125.4.196): unknown user:
dovecot: auth: ldap(lane,185.125.4.196): unknown user:
dovecot: auth: ldap(language,185.125.4.196): unknown user:
dovecot: auth: ldap(larkin,185.125.4.196): unknown user:
dovecot: auth: ldap(laurie,185.125.4.196): unknown user:
dovecot: auth: ldap(leadership,193.189.117.156): unknown user:
dovecot: auth: ldap(lenny,185.125.4.196): unknown user:
dovecot: auth: ldap(lenovo,193.189.117.156): unknown user:
dovecot: auth: ldap(leslie,193.189.117.156): unknown user:
dovecot: auth: ldap(level,185.125.4.196): unknown user:
dovecot: auth: ldap(levi,185.125.4.196): unknown user:
dovecot: auth: ldap(libby,185.125.4.196): unknown user:
dovecot: auth: ldap(liliana,193.189.117.156): unknown user:
dovecot: auth: ldap(lina,193.189.117.147): unknown user:
dovecot: auth: ldap(linda,193.189.117.147): unknown user:
dovecot: auth: ldap(lisette,185.125.4.196): unknown user:
dovecot: auth: ldap(local,193.189.117.156): unknown user:
dovecot: auth: ldap(log,193.189.117.151): unknown user:
dovecot: auth: ldap(logs,193.189.117.148): unknown user:
dovecot: auth: ldap(lori,193.189.117.156): unknown user:
dovecot: auth: ldap(louis,193.189.117.156): unknown user:
dovecot: auth: ldap(luciano,193.189.117.148): unknown user:
dovecot: auth: ldap(magdalena,193.189.117.151): unknown user:
dovecot: auth: ldap(maggie,193.189.117.156): unknown user:
dovecot: auth: ldap(main,193.189.117.149): unknown user:
dovecot: auth: ldap(maint,193.189.117.151): unknown user:
dovecot: auth: ldap(management,193.189.117.156): unknown user:
dovecot: auth: ldap(manolo,193.189.117.156): unknown user:
dovecot: auth: ldap(manzanares,193.189.117.156): unknown user:
dovecot: auth: ldap(marcos,193.189.117.151): unknown user:
dovecot: auth: ldap(mariana,193.189.117.149): unknown user:
dovecot: auth: ldap(marion,193.189.117.156): unknown user:
dovecot: auth: ldap(marisa,193.189.117.151): unknown user:
dovecot: auth: ldap(marna,193.189.117.147): unknown user:
dovecot: auth: ldap(martina,193.189.117.156): unknown user:
dovecot: auth: ldap(mat,193.189.117.149): unknown user:
dovecot: auth: ldap(matt,193.189.117.147): unknown user:
dovecot: auth: ldap(mauricio,193.189.117.151): unknown user:
dovecot: auth: ldap(mauro,193.189.117.151): unknown user:
dovecot: auth: ldap(max,193.189.117.151): unknown user:
dovecot: auth: ldap(maximo,193.189.117.156): unknown user:
dovecot: auth: ldap(may,193.189.117.147): unknown user:
dovecot: auth: ldap(mendoza,193.189.117.151): unknown user:
dovecot: auth: ldap(mercadeo,193.189.117.148): unknown user:
dovecot: auth: ldap(mercado,193.189.117.156): unknown user:
dovecot: auth: ldap(meridian,193.189.117.156): unknown user:
dovecot: auth: ldap(message,193.189.117.156): unknown user:
dovecot: auth: ldap(mexico,193.189.117.156): unknown user:
dovecot: auth: ldap(michelle,193.189.117.149): unknown user:
dovecot: auth: ldap(miguel,193.189.117.148): unknown user:
dovecot: auth: ldap(mimi,193.189.117.156): unknown user:
dovecot: auth: ldap(mirella,193.189.117.156): unknown user:
dovecot: auth: ldap(modem,193.189.117.156): unknown user:
dovecot: auth: ldap(montero,185.125.4.191): unknown user:
dovecot: auth: ldap(morales,185.125.4.191): unknown user:
dovecot: auth: ldap(moreno,193.189.117.156): unknown user:
dovecot: auth: ldap(muriel,193.189.117.156): unknown user:
dovecot: auth: ldap(mysql,193.189.117.149): unknown user:
dovecot: auth: ldap(nadia,185.125.4.191): unknown user:
dovecot: auth: ldap(nandi,185.125.4.191): unknown user:
dovecot: auth: ldap(naranjo,193.189.117.156): unknown user:
dovecot: auth: ldap(nathalie,193.189.117.149): unknown user:
dovecot: auth: ldap(nathan,185.125.4.191): unknown user:
dovecot: auth: ldap(nava,185.125.4.191): unknown user:
dovecot: auth: ldap(neil,185.125.4.191): unknown user:
dovecot: auth: ldap(neptune,185.125.4.191): unknown user:
dovecot: auth: ldap(network,193.189.117.156): unknown user:
dovecot: auth: ldap(new,193.189.117.148): unknown user:
dovecot: auth: ldap(newton,185.125.4.191): unknown user:
dovecot: auth: ldap(nicholas,185.125.4.191): unknown user:
dovecot: auth: ldap(nichole,193.189.117.156): unknown user:
dovecot: auth: ldap(nicole,193.189.117.148): unknown user:
dovecot: auth: ldap(nikki,193.189.117.156): unknown user:
dovecot: auth: ldap(nina,193.189.117.149): unknown user:
dovecot: auth: ldap(noc,193.189.117.148): unknown user:
dovecot: auth: ldap(norma,193.189.117.156): unknown user:
dovecot: auth: ldap(norton,193.189.117.156): unknown user:
dovecot: auth: ldap(oleg,193.189.117.156): unknown user:
dovecot: auth: ldap(orlando,185.125.4.191): unknown user:
dovecot: auth: ldap(pablo,193.189.117.148): unknown user:
dovecot: auth: ldap(paige,185.125.4.191): unknown user:
dovecot: auth: ldap(paolo,193.189.117.152): unknown user:
dovecot: auth: ldap(password,185.125.4.191): unknown user:
dovecot: auth: ldap(pat,193.189.117.152): unknown user:
dovecot: auth: ldap(patricia,185.125.4.191): unknown user:
dovecot: auth: ldap(patty,185.125.4.191): unknown user:
dovecot: auth: ldap(payment,185.125.4.191): unknown user:
dovecot: auth: ldap(paz,185.125.4.191): unknown user:
dovecot: auth: ldap(pc03,193.189.117.152): unknown user:
dovecot: auth: ldap(pereira,185.125.4.197): unknown user:
dovecot: auth: ldap(perfil,193.189.117.152): unknown user:
dovecot: auth: ldap(perl,185.125.4.197): unknown user:
dovecot: auth: ldap(perry,185.125.4.191): unknown user:
dovecot: auth: ldap(pharmacy,185.125.4.191): unknown user:
dovecot: auth: ldap(philip,193.189.117.152): unknown user:
dovecot: auth: ldap(phoenix,193.189.117.152): unknown user:
dovecot: auth: ldap(physics,185.125.4.197): unknown user:
dovecot: auth: ldap(pics,185.125.4.197): unknown user:
dovecot: auth: ldap(pie,185.125.4.197): unknown user:
dovecot: auth: ldap(pina,185.125.4.197): unknown user:
dovecot: auth: ldap(place,185.125.4.191): unknown user:
dovecot: auth: ldap(plant,185.125.4.191): unknown user:
dovecot: auth: ldap(point,185.125.4.197): unknown user:
dovecot: auth: ldap(police,185.125.4.191): unknown user:
dovecot: auth: ldap(politics,185.125.4.191): unknown user:
dovecot: auth: ldap(polly,185.125.4.197): unknown user:
dovecot: auth: ldap(pool,185.125.4.191): unknown user:
dovecot: auth: ldap(pop3,185.125.4.197): unknown user:
dovecot: auth: ldap(portatil,193.189.117.148): unknown user:
dovecot: auth: ldap(poster,185.125.4.191): unknown user:
dovecot: auth: ldap(pot,185.125.4.197): unknown user:
dovecot: auth: ldap(potato,185.125.4.197): unknown user:
dovecot: auth: ldap(power,185.125.4.191): unknown user:
dovecot: auth: ldap(practice,185.125.4.197): unknown user:
dovecot: auth: ldap(praise,185.125.4.197): unknown user:
dovecot: auth: ldap(president,185.125.4.197): unknown user:
dovecot: auth: ldap(prince,185.125.4.191): unknown user:
dovecot: auth: ldap(priority,185.125.4.197): unknown user:
dovecot: auth: ldap(process,185.125.4.197): unknown user:
dovecot: auth: ldap(profesor,185.125.4.191): unknown user:
dovecot: auth: ldap(professional,185.125.4.197): unknown user:
dovecot: auth: ldap(professor,193.189.117.154): unknown user:
dovecot: auth: ldap(profile,193.189.117.152): unknown user:
dovecot: auth: ldap(promise,185.125.4.197): unknown user:
dovecot: auth: ldap(protocol,185.125.4.197): unknown user:
dovecot: auth: ldap(proyecto,193.189.117.152): unknown user:
dovecot: auth: ldap(ps,193.189.117.147): unknown user:
dovecot: auth: ldap(puertas,185.125.4.191): unknown user:
dovecot: auth: ldap(python,185.125.4.197): unknown user:
dovecot: auth: ldap(qtss,193.189.117.154): unknown user:
dovecot: auth: ldap(rabia,185.125.4.197): unknown user:
dovecot: auth: ldap(rack,185.125.4.197): unknown user:
dovecot: auth: ldap(rae,185.125.4.197): unknown user:
dovecot: auth: ldap(ralph,185.125.4.191): unknown user:
dovecot: auth: ldap(ram,185.125.4.191): unknown user:
dovecot: auth: ldap(ramiro,193.189.117.154): unknown user:
dovecot: auth: ldap(raquel,185.125.4.197): unknown user:
dovecot: auth: ldap(ray,193.189.117.152): unknown user:
dovecot: auth: ldap(read,185.125.4.197): unknown user:
dovecot: auth: ldap(reality,185.125.4.197): unknown user:
dovecot: auth: ldap(rebecca,193.189.117.154): unknown user:
dovecot: auth: ldap(rechnung,193.189.117.154): unknown user:
dovecot: auth: ldap(recording,185.125.4.197): unknown user:
dovecot: auth: ldap(recover,185.125.4.197): unknown user:
dovecot: auth: ldap(red,193.189.117.154): unknown user:
dovecot: auth: ldap(reed,185.125.4.197): unknown user:
dovecot: auth: ldap(reference,185.125.4.197): unknown user:
dovecot: auth: ldap(register,193.189.117.154): unknown user:
dovecot: auth: ldap(registro,193.189.117.147): unknown user:
dovecot: auth: ldap(remoto,193.189.117.152): unknown user:
dovecot: auth: ldap(ricky,193.189.117.148): unknown user:
dovecot: auth: ldap(robin,193.189.117.147): unknown user:
dovecot: auth: ldap(rocio,193.189.117.154): unknown user:
dovecot: auth: ldap(roger,193.189.117.148): unknown user:
dovecot: auth: ldap(roman,193.189.117.154): unknown user:
dovecot: auth: ldap(rosario,193.189.117.154): unknown user:
dovecot: auth: ldap(ruben,193.189.117.147): unknown user:
dovecot: auth: ldap(sales1,193.189.117.152): unknown user:
dovecot: auth: ldap(sally,193.189.117.152): unknown user:
dovecot: auth: ldap(sam,193.189.117.148): unknown user:
dovecot: auth: ldap(samantha,193.189.117.154): unknown user:
dovecot: auth: ldap(sandi,193.189.117.154): unknown user:
dovecot: auth: ldap(sandra,193.189.117.148): unknown user:
dovecot: auth: ldap(sandy,193.189.117.148): unknown user:
dovecot: auth: ldap(sarah,193.189.117.147): unknown user:
dovecot: auth: ldap(schmidt,193.189.117.152): unknown user:
dovecot: auth: ldap(sean,193.189.117.152): unknown user:
dovecot: auth: ldap(sensor,193.189.117.154): unknown user:
dovecot: auth: ldap(seo,193.189.117.148): unknown user:
dovecot: auth: ldap(share,193.189.117.147): unknown user:
dovecot: auth: ldap(sharon,193.189.117.152): unknown user:
dovecot: auth: ldap(ship,193.189.117.152): unknown user:
dovecot: auth: ldap(simon,193.189.117.147): unknown user:
dovecot: auth: ldap(smile,193.189.117.154): unknown user:
dovecot: auth: ldap(spam,81.168.60.61): unknown user:
dovecot: auth: ldap(spam@balaskas.gr,81.168.60.61): unknown user:
dovecot: auth: ldap(spectrum,193.189.117.147): unknown user:
dovecot: auth: ldap(sql,193.189.117.147): unknown user:
dovecot: auth: ldap(sqlservice,193.189.117.147): unknown user:
dovecot: auth: ldap(staging,193.189.117.152): unknown user:
dovecot: auth: ldap(standard,193.189.117.154): unknown user:
dovecot: auth: ldap(studio,193.189.117.154): unknown user:
dovecot: auth: ldap(summer,193.189.117.152): unknown user:
dovecot: auth: ldap(sunny,193.189.117.152): unknown user:
dovecot: auth: ldap(sync,193.189.117.154): unknown user:
dovecot: auth: ldap(tania,193.189.117.147): unknown user:
dovecot: auth: ldap(tatiana,193.189.117.154): unknown user:
dovecot: auth: ldap(tax,193.189.117.152): unknown user:
dovecot: auth: ldap(telecomunicaciones,193.189.117.152): unknown user:
dovecot: auth: ldap(test@balaskas.gr,89.248.162.175): unknown user:
dovecot: auth: ldap(testpc,193.189.117.154): unknown user:
dovecot: auth: ldap(tools,193.189.117.152): unknown user:
dovecot: auth: ldap(touch,185.125.4.198): unknown user:
dovecot: auth: ldap(tower,185.125.4.198): unknown user:
dovecot: auth: ldap(traci,185.125.4.198): unknown user:
dovecot: auth: ldap(tracy,193.189.117.154): unknown user:
dovecot: auth: ldap(trade,185.125.4.198): unknown user:
dovecot: auth: ldap(traffic,185.125.4.198): unknown user:
dovecot: auth: ldap(train,193.189.117.152): unknown user:
dovecot: auth: ldap(treasure,185.125.4.198): unknown user:
dovecot: auth: ldap(tristan,185.125.4.198): unknown user:
dovecot: auth: ldap(troy,193.189.117.154): unknown user:
dovecot: auth: ldap(trujillo,185.125.4.198): unknown user:
dovecot: auth: ldap(truman,185.125.4.198): unknown user:
dovecot: auth: ldap(ts,193.189.117.154): unknown user:
dovecot: auth: ldap(tucker,185.125.4.198): unknown user:
dovecot: auth: ldap(tyler,185.125.4.198): unknown user:
dovecot: auth: ldap(type,185.125.4.198): unknown user:
dovecot: auth: ldap(ubuntu,193.189.117.154): unknown user:
dovecot: auth: ldap(unicorn,193.189.117.154): unknown user:
dovecot: auth: ldap(union,185.125.4.198): unknown user:
dovecot: auth: ldap(upgrade,193.189.117.154): unknown user:
dovecot: auth: ldap(usuarioprueba,185.125.4.198): unknown user:
dovecot: auth: ldap(uucp,185.125.4.198): unknown user:
dovecot: auth: ldap(val,185.125.4.198): unknown user:
dovecot: auth: ldap(valenzuela,185.125.4.198): unknown user:
dovecot: auth: ldap(valeria,185.125.4.198): unknown user:
dovecot: auth: ldap(valerie,193.189.117.154): unknown user:
dovecot: auth: ldap(valerio,185.125.4.198): unknown user:
dovecot: auth: ldap(value,185.125.4.198): unknown user:
dovecot: auth: ldap(vanessa,193.189.117.152): unknown user:
dovecot: auth: ldap(vector,185.125.4.198): unknown user:
dovecot: auth: ldap(venta,193.189.117.154): unknown user:
dovecot: auth: ldap(ventas2,193.189.117.154): unknown user:
dovecot: auth: ldap(vente,185.125.4.198): unknown user:
dovecot: auth: ldap(verhaal,185.125.4.198): unknown user:
dovecot: auth: ldap(veronique,185.125.4.198): unknown user:
dovecot: auth: ldap(vincenzo,185.125.4.198): unknown user:
dovecot: auth: ldap(virgil,185.125.4.198): unknown user:
dovecot: auth: ldap(vnc,193.189.117.152): unknown user:
dovecot: auth: ldap(voice,185.125.4.198): unknown user:
dovecot: auth: ldap(wall,185.125.4.198): unknown user:
dovecot: auth: ldap(walter,193.189.117.152): unknown user:
dovecot: auth: ldap(watch,185.125.4.198): unknown user:
dovecot: auth: ldap(water,193.189.117.154): unknown user:
dovecot: auth: ldap(wave,185.125.4.198): unknown user:
dovecot: auth: ldap(webmaster,104.160.176.218): unknown user:
dovecot: auth: ldap(webmaster@balaskas.gr,104.160.176.218): unknown user:
dovecot: auth: ldap(william,193.189.117.154): unknown user:
dovecot: auth: ldap(x,193.189.117.152): unknown user:
Reading through “Smart Girl’s Guide to Privacy - Practical Tips for Staying Safe Online by Violet Blue” (totally recommend it), there is a great tip in the first few pages:
- Use different email addresses for different online accounts.
… but is it possible ?
Different Passwords
We already know that we need to use a different password for every site. So we use lastpass or password managers for keeping our different passwords safe. We are nowadays used to create/generate complex passwords for every site, but is it absolutely necessary to also have a different email address for every single one ?
Different Email Addresses
Let me be as clear as I can: There is no obvious answer.
If you value your online privacy and your security threat model is set really high, then Yes you also need a different email address.
But it depends entirely on you and how you use your online identity. Perhaps in social media sites (like facebook or twitter) you dont need to give your personal email address, but perhaps on linkedin you want to use your well-known email-identity. So again, it depends on your security thread model.
Another crucial tip: DO NOT cross-connect your online personas from different social medias.
Disposable Email Server
In this blog post, I will try to describe the simple steps you need to take, to create your own personal disposable email server. In simple words, that means that you can dynamically create and use a unique/specific-site-only email address that you can use for sign-up or register to a new site. Using a different email address & a different passwords for every site online, you are making it really difficult for someone to hack you.
Even if someone can get access to this specific website or -somehow- can retrieve your online account (sites are been hacked every day), you are sure that none of your other online accounts/identities can not be accessed too.
DOMAIN
To do that you will need a disposable domain. It does not have to be something clever or even useful. It needs to be something easy to write & remember. In my opinion, just get a cheap domain. If your registar support WHOIS Privacy, then even better. If dont, then try to find a registar that supports WHOIS Privacy but it isnt a blocking issue.
For this blog post I will use: example.org
Catch-All
In theory, we will create a “catch-all” domain/mail server, that will catch and forward all these emails to our current/primary email address.
DNS
So nice, you have a disposable domain. What next ?
You need to setup a new domain dns zone for your disposable domain.
And then add a MX record, like the notes below:
example.org. 86400 IN MX 0 mail.example.org.
mail.example.org. 86400 IN A 1.2.3.4
replace 1.2.3.4 with the server’s IP !!
Mail Server
Just install postfix !
My “notable” settings are these below:
# postconf -n
inet_interfaces = all
inet_protocols = all
message_size_limit = 35651584
smtp_address_preference = ipv6
smtpd_banner = The sky above the port was the color of television, tuned to a dead channel
virtual_alias_domains = example.org
virtual_alias_maps = hash:/etc/postfix/virtual
In my /etc/postfix/virtual I have these lines:
@example.org my_email_address@example.net
(dont forget to postmap and reload)
# postmap /etc/postfix/virtual
# postfix reload
…. and …. that is it, actually !!!
a. Be aware the my disposable email server is dual stack.
b. If you need to create an emailing list, try something like this:
list@example.org my_email_address@example.net, my_other_email_address@gmail.com
dont forget to:
# postmap /etc/postfix/virtual
and reload postfix:
# postfix reload
How to use it
From now on, whenever you need to type an email address somewhere, just type a new (random or not) email address with this new disposable domain.
The catch-all setting will FWD any email to your primary email address.
I like to use the below specific pattern: When you need to sign-up to a new site, use the sites url as your new email address.
eg. twitter.com
twittercom@example.org
It’s now obvious that next time you get SPAM, you will know which one to blame (I am not suggesting that twitter is sending spam, it is just an example!).
You can also change your email address from all the sites that you have already subscribe (github, mailing lists, etc etc).
Hope this post has been helpful and easy enough for everyone.
Google Reader was -of general acceptance- the best RSS feed reader.
Yahoo had it’s own “perfect” project to parse feeds: Yahoo! Pipes
What did both projects have in common?
They both were cloud projects
that are now discontinued
cause their companies could not profit from them !!!
FreshRSS
So a lot of people started to look up on self-hosted RSS readers to overcome this issue.
Below are my notes on FreshRSS , a free, self-hostable aggregator…
First, download the latest version of FreshRSS:
Download and Setup
# wget -c https://github.com/FreshRSS/FreshRSS/archive/master.zip
# unzip master.zip
# mv FreshRSS-master/ FreshRSS
# chown -R apache:apache FreshRSS
apache
Create a new Virtual Host on apache and use Let’s Encrypt to create a new SSL certificate:
< VirtualHost *:443 >
ServerName FreshRSS.example.com
# SSL Support
SSLEngine on
SSLProtocol ALL -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite HIGH:!aNULL:!MD5
SSLCertificateFile /etc/letsencrypt/live/FreshRSS.example.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/FreshRSS.example.com/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/FreshRSS.example.com/chain.pem
# Logs
CustomLog logs/FreshRSS.access.log combined
ErrorLog logs/FreshRSS.error.log
DocumentRoot /var/www/html/FreshRSS/
< Directory /var/www/html/FreshRSS/ >
Order allow,deny
Allow from all
< /Directory >
< /VirtualHost >
reload your apache and after that, open your browser to begin the installation process.
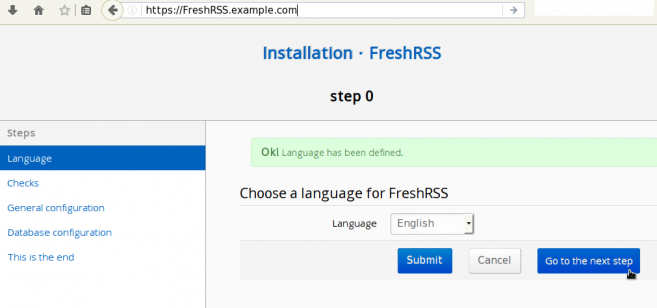
Installation
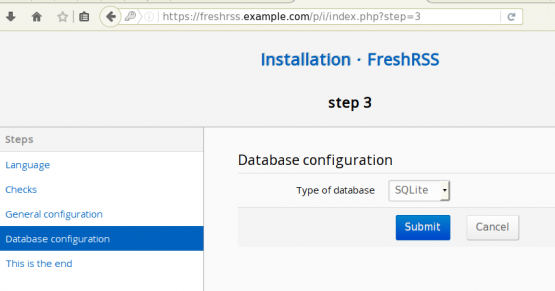
SQLite Backend
I prefer to use SQLite for my backend self-hosted projects, cause the backup process is a lot easier than with mysql.
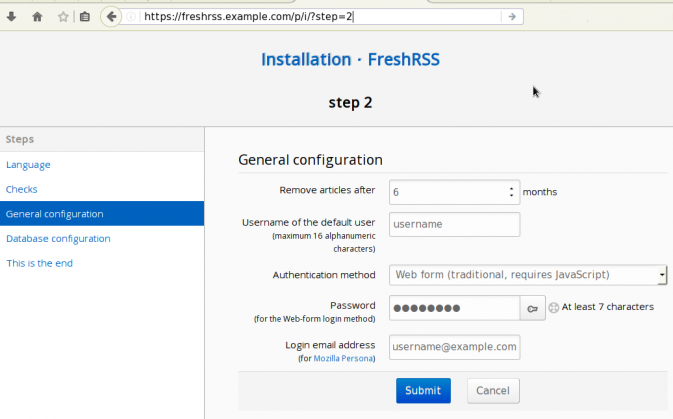
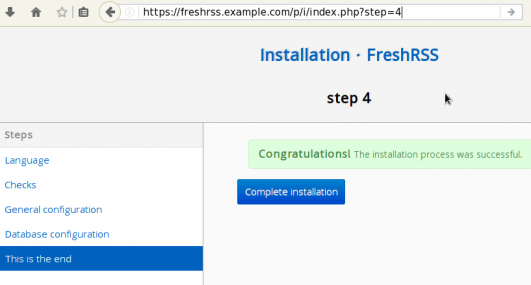
At this point you have a fresh FreshRSS installation (self-hosted) on your server!
If you just want to use it through your browser, you are done.
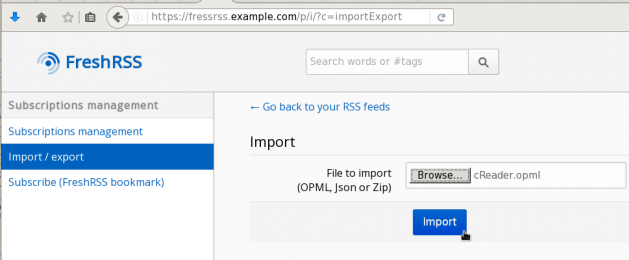
OPML
If you already have a OPML (Outline Processor Markup Language) file with your rss/atom feeds, then you can upload it (import) through the Subscription Manager:
Feeds - Automated Updates
So conclude our FreshRSS setup, we need to automate the update of our feeds. To do that, we just need to add a cron script.
# vim /etc/crontab
*/15 * * * * apache /usr/bin/php /var/www/html/FreshRSS//app/actualize_script.php &> /tmp/fresh.log
EasyRSS
What about your android device (smart phone or tablet) ?
You can use EasyRSS !
Just install it from Fdroid and run it:
FreshRSS - API
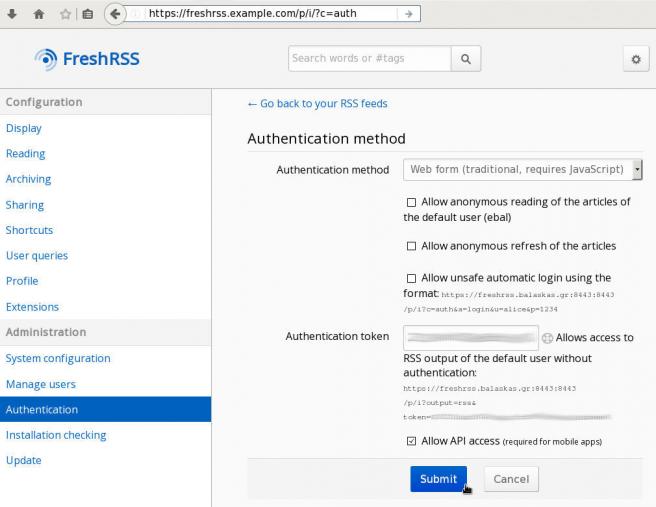
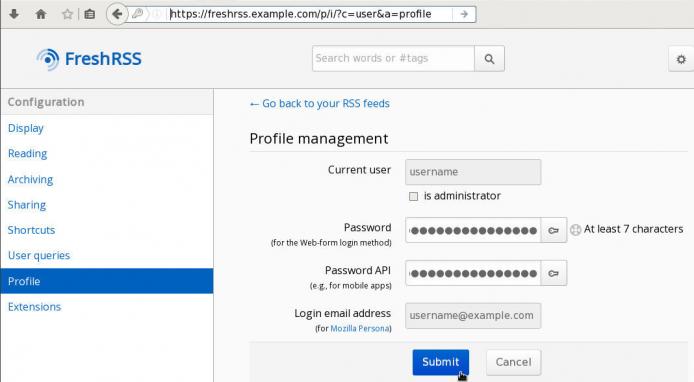
To use EasyRSS with FreshRSS, you need to enable the API support from FreshRSS.
The EasyRSS then, will use the api through a token, so to keep things simple enough, we will also change our password to the token ID.
So go to Settings —> Authentication and enable:
Allow API access (required for mobile apps)
Then go to Settings –> Profile and change your password too:
After that, you can now type your settings on your EasyRSS app:
https://freshrss.example.com/p/api/greader.php
Below is my setup to enable Forward secrecy
Generate DH parameters:
# openssl dhparam -out /etc/pki/tls/dh-2048.pem 2048
and then configure your prosody with Let’s Encrypt certificates
VirtualHost "balaskas.gr"
ssl = {
key = "/etc/letsencrypt/live/balaskas.gr/privkey.pem";
certificate = "/etc/letsencrypt/live/balaskas.gr/fullchain.pem";
cafile = "/etc/pki/tls/certs/ca-bundle.crt";
# enable strong encryption
ciphers="EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!RC4";
dhparam = "/etc/pki/tls/dh-2048.pem";
}
if you only want to accept TLS connection from clients and servers, change your settings to these:
c2s_require_encryption = true
s2s_secure_auth = true
Check your setup
or check your certificates with openssl:
Server: # openssl s_client -connect balaskas.gr:5269 -starttls xmpp < /dev/null
Client: # openssl s_client -connect balaskas.gr:5222 -starttls xmpp < /dev/null
Top Ten Linux Distributions and https
A/A | Distro | URL | Verified by | Begin | End | Key
01. | ArchLinux | https://www.archlinux.org/ | Let's Encrypt | 02/24/2016 | 05/24/2016 | 2048
02. | Linux Mint | https://linuxmint.com/ | COMODO CA Limited | 02/24/2016 | 02/24/2017 | 2048
03. | Debian | https://www.debian.org/ | Gandi | 12/11/2015 | 01/21/2017 | 3072
04. | Ubuntu | http://www.ubuntu.com | - | - | - | -
05. | openSUSE | https://www.opensuse.org/ | DigiCert Inc | 02/17/2015 | 04/23/2018 | 2048
06. | Fedora | https://getfedora.org/ | DigiCert Inc | 11/24/2014 | 11/28/2017 | 4096
07. | CentOS | https://www.centos.org/ | DigiCert Inc | 07/29/2014 | 08/02/2017 | 2048
08. | Manjaro | https://manjaro.github.io/ | DigiCert Inc | 01/20/2016 | 04/06/2017 | 2048
09. | Mageia | https://www.mageia.org/ | Gandi | 03/01/2016 | 02/07/2018 | 2048
10. | Kali | https://www.kali.org/ | GeoTrust Inc | 11/09/2014 | 11/12/2018 | 2048
Baïkal is a CalDAV and CardDAV server, based on sabre/dav,
To self hosted your own CalDAV & CardDAV server is one of the first step to better control your data and keep your data, actually, yours!So here comes Baikal which is really easy to setup. That easily you can also configure any device (mobile/tablet/laptop/desktop) to use your baikal instance and synchronize your calendar & contacts everywhere.
In this blog post are some personal notes on installing or upgrading baikal on your web server.
[ The latest version as this article was written is 0.4.1 ]
Change to your web directory (usually is something like: /var/www/html/) and download baikal:
Clean Install - Latest release 0.4.1
based on sabre/dav 3.1.2
You need at least PHP 5.5 but preferable use 5.6.
# wget -c https://github.com/fruux/Baikal/releases/download/0.4.1/baikal-0.4.1.zip
# yes | unzip baikal-0.4.1.zip
# chown -R apache:apache baikal/
That’s it !
Be Aware that there is a big difference between 0.2.7 and versions greater that 0.3.x.
And that is, that the URL has an extra part: htmlfrom: https://baikal.example.com/admin
to : https://baikal.example.com/html/admin
If you already had installed baikal-0.2.7 and you want to upgrade to 0.4.x version and later, then you have to follow the below steps:
# wget -c http://baikal-server.com/get/baikal-flat-0.2.7.zip
# unzip baikal-flat-0.2.7.zip
# mv baikal-flat baikal
# wget -c https://github.com/fruux/Baikal/releases/download/0.4.1/baikal-0.4.1.zip
# yes | unzip baikal-0.4.1.zip
# touch baikal/Specific/ENABLE_INSTALL
# chown -R apache:apache baikal/
I prefer to create a new virtualhost every time I need to add a new functionality to my domain.
Be smart & use encryption !
Below is mine virtualhost as an example:
< VirtualHost *:443 >
ServerName baikal.example.com
# SSL Support
SSLEngine on
SSLProtocol ALL -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite HIGH:!aNULL:!MD5
SSLCertificateFile /etc/letsencrypt/live/baikal.example.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/baikal.example.com/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/baikal.example.com/chain.pem
# Logs
CustomLog logs/baikal.access.log combined
ErrorLog logs/baikal.error.log
DocumentRoot /var/www/html/baikal/
< Directory /var/www/html/baikal/ >
Order allow,deny
Allow from all
< /Directory >
< /VirtualHost >
Next step is to open your browser and browse your baikal's location,
eg. https://baikal.example.com/html/
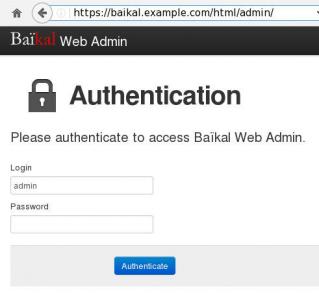
admin interface:
https://baikal.example.com/html/admin/
or
if you have an older version (0.2.7) on your system
eg. https://baikal.example.com
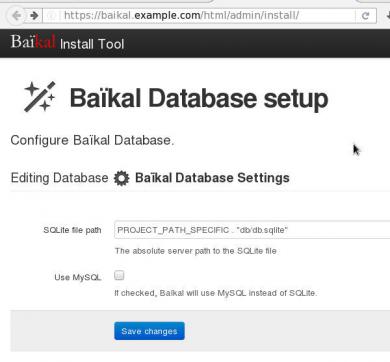
I use SQLite for personal use (makes easy backup process) but you can always choose MySQL .
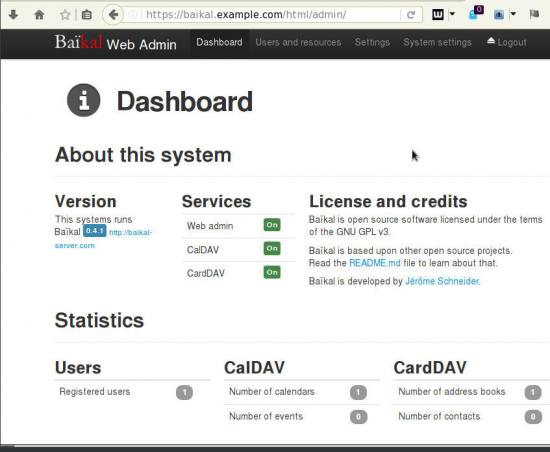
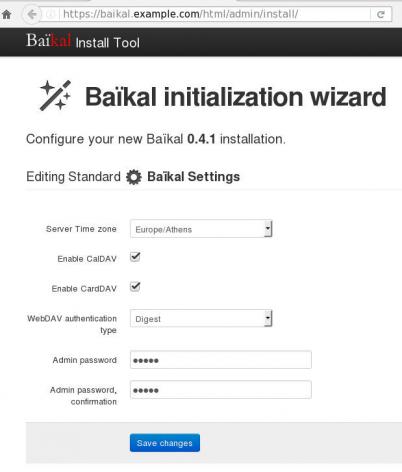
Dashboard on 0.4.1
Useful URIs are:
Principals:
Plugins:
Nodes:
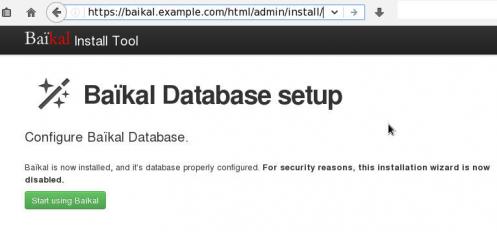
Here is a sceen-guide on latest versions:
Login to the admin dashboard and create your user through
Users and resources tab
and you are done with the baikal installation & configuration process.
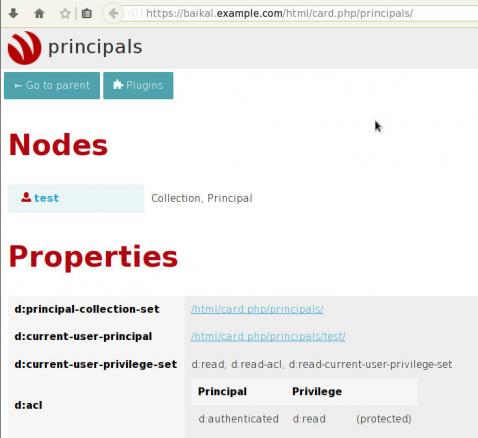
Principals
Applications (caldav/carddav and task clients) can now be accessed by visiting principals URI:
https://baikal.example.com/html/card.php/principals
or via dav.php
https://baikal.example.com/html/dav.php
but If your client does not support the above holistic URI, then try the below for calendar & contacts:
CalDAV
https://baikal.example.com/html/cal.php/calendars/test/default
CardDAV
https://baikal.example.com/html/card.php/addressbooks/test/default
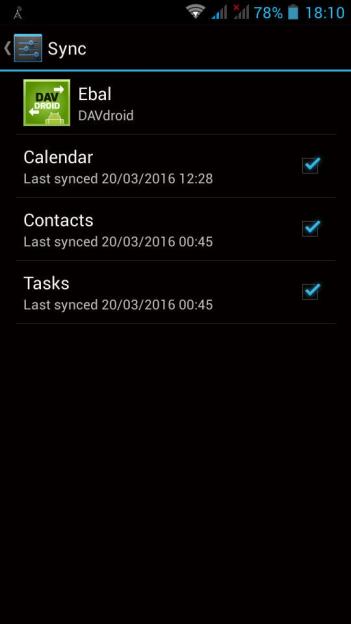
On android devices, I use: DAVdroid
If you have a problem with your self-signed certificate,
try adding it to your device through the security settings.
I’ve started a new project with bottle.py and had some hiccups with static files and templates.
My project layout is (something) like that:
/
app.wsgi
bottle.py
static/
static/css
static/css/bootstrap-theme.min.css
static/css/bootstrap.min.css
static/img
static/img/logo.png
static/js
static/js/bootstrap.min.js
static/js/npm.js
static/js/tab.js
static/js/jquery-1.12.1.min.js
views/
views/search.tpl
views/index.tpl
views/header.tpl
views/footer.tpl
my app.wsgi is looking something like (dynamic routes & templates):
@bottle.route('/')
@bottle.route('/< action >/< name >')
def main(action='/',name=None):
if ( action == '/' ) :
return template("index", title=" some title ")
else:
return template(action, title=" some title ", name=name)
application = bottle.default_app()
I can translate every REST request to a new template and use AJAX inside the templates.
But what-about static files like stylesheets and javascripts ?
eg.
< script src="jquery-1.12.1.min.js"> < / script>
< img src="logo_hp.png" >
When working with dynamic routes (or any routes in bottle) unless you are using the main app.wsgi everything else will be translated to something like:
GET /search/jquery-1.12.1.min.js
GET /view/jquery-1.12.1.min.js
etc
If you noticed the layout then somehow we need to map all static files (css,js,images) to our static folder. We can map static files from "/" with the code below:
@bottle.get('< filename:re:.*.js >')
def static_js(filename):
return static_file(filename, root='static/js')
@bottle.get(' < filename:re:.*.css > ')
def static_css(filename):
return static_file(filename, root='static/css')
@bottle.get(' < filename:re:.*.png > ')
def static_img(filename):
return static_file(filename, root='static/img')
Ok, that worked for the initial route (index page) but what about all the other templates & requests?
The solution was really (really) very very simply, even if it took me a couple hours to figure it out!!
I just needed to add a forward slash in front of every static file:
< script src="/jquery-1.12.1.min.js"> < / script>
< img src="/logo.png" >
and the GET request becomes:
"GET /jquery-1.12.1.min.js
and we can now route the static files to our static file directory.
I spent a lot of time on commute, so the last year I’ve spent a lot of time listening to podcasts and audio books!
Here are the latest books (in random order) I’ve heard:

Little Brother by Cory Doctorow
Information Doesn’t Want to Be Free by Cory Doctorow

The Hitchhiker’s Guide to the Galaxy (radio edition) by Douglas Adams
debootstrap is a very powerful tool that most of debian/ubuntu people already know about.
It’s really super easy to create your own basic debian docker image, even if you are not running debian.
I used the below steps to my archlinux box, but i believe are generic and you can also use them, without any effort.
Step One:
Download and prepare debootstrap
# wget -c http://ftp.debian.org/debian/pool/main/d/debootstrap/debootstrap_1.0.77.tar.gz
# tar xf debootstrap_*.tar.gz
# cd debootstrap
# sed -i -e 's#/usr/share/debootstrap#.#' debootstrap
Step Two:
debootstrap a new sid (unstable) debian:
# mkdir sid
# ./debootstrap --arch amd64 --include=aptitude sid sid/
Step Three:
Just to be safe, extract debian packages with ar
# cd sid
# for i in `ls -1 var/cache/apt/archives/*deb`; do ar p $i data.tar.xz | tar xJ ; done
# for i in `ls -1 var/cache/apt/archives/*deb`; do ar p $i data.tar.gz | tar xz ; done
# rm -rf var/cache/apt/archives/*deb
Step Four:
Prepare your debian unstable directory.
eg. create the sources.list file
# cat > etc/apt/sources.list << EOF
> deb http://ftp.gr.debian.org/debian unstable main contrib non-free
> deb http://ftp.debian.org/debian/ Sid-updates main contrib non-free
> deb http://security.debian.org/ Sid/updates main contrib non-free
> EOF
Step Five:
Dockerized your debian image:
# tar -c . | docker import - debian:sid
cdf6f22b76f23fa95ae2d5858cec4546086a2064b66cf34b937bc87c83f13c91
# docker images
REPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZE
debian sid cdf6f22b76f2 5 seconds ago 291.3 MB
You are now ready to play with your new image:
# docker run -t -i --rm debian:sid bash
I have no name!@f3ee67226a07:/#
Some time ago, I wrote this article: How to create an archlinux docker image from the latest bootstrap but I think the below approach is even better.
Step 0
This step is optional.
If you want to reduce the size of the docker image:
# vi /etc/pacman.conf
and add the below lines:
NoExtract = usr/lib/firmware/*
NoExtract = usr/lib/modules/*
NoExtract = usr/share/locale/*
NoExtract = usr/share/man/*
Step 1
Create the latest archlinux on a temporary directory:
# mkdir -pv /tmp/latestarchlinux/var/lib/pacman
# pacman -Syy -r /tmp/latestarchlinux/
# pacman -S base -r /tmp/latestarchlinux/ --noconfirm
Step 2
dockerized the above directory
# cd /tmp/latestarchlinux/
# tar -c . | docker import - archlinux:latest
99a9d7cd2e357f2463b4bb8f3ad1e8bea4bfc10531dfac1931004405727bf035
Step 3
Actually you ‘ve done !
Just play with it already.
# docker run -t -i --rm archlinux:latest bash
[root@de9b7a1d6058 /]#
I am not trying to resolv this issue, I have lost any faith on sourceforge a long time ago.
Although, it is sad. Once, if you wanted to download free software for your linux machine, SF was the place to be.
Nowadays the site is awful. You cant even browse the site if you dont use an ad-blocker.
It is chaotic with all these features and extremely painful if you actually try to do something, even if it is the simplest thing like changing your email address.
This post is just a personal rant about SF subscriptions and nothing more.
I have changed my email address on sourceforge for about a year now. Still I am getting subscription notifies from projects to my previous (deprecated) mail address:
…. so …. yes …
by clicking on the “Manage your subscriptions” link on the bottom of the notify email:
seems that I dont have any project subscriptions !
And that’s not even the big issue here, cause I do want to get notifies whenever SystemRescueCD do updates.
The big issue, for me at least, is when I tried to subscribe on SystemRescueCD (thinking that at least now the notifies will come to my new email address):
If you missed it, the problem is with this quote below:
sponsored content from our select partners, and more
sourceforge simple dont get it !
A colleague asked me to install MySQL UDF (MySQL user defined functions) on a server.
So here are my notes on the subject, for a CentOS 6.7 linux box:
First you need to have mysql-devel on your system which install the mysql development headers on /usr/include/mysql/ directory:
# yum -y install mysql-devel
Then download the latest source code of mysqludf_udf:
# wget -c https://raw.githubusercontent.com/mysqludf/lib_mysqludf_udf/master/lib_mysqludf_udf.c
and compile it
# gcc -m64 -fPIC -Wall
-I/usr/include/mysql -I.
-L/usr/lib64/libstdc++.so.6
-shared lib_mysqludf_udf.c
-o /usr/lib64/mysql/plugin/lib_mysqludf_udf.so
confirm:
# ls -l /usr/lib64/mysql/plugin/lib_mysqludf_udf.so
Restart your MySQL and test it !
CPU
# cat /proc/cpuinfo
Processor : ARMv7 Processor rev 1 (v7l)
processor : 0
BogoMIPS : 3.27
processor : 1
BogoMIPS : 3.27
processor : 2
BogoMIPS : 3.27
processor : 3
BogoMIPS : 3.27
Features : swp half thumb fastmult vfp edsp neon vfpv3 tls vfpv4
CPU implementer : 0x41
CPU architecture: 7
CPU variant : 0x0
CPU part : 0xc05
CPU revision : 1
Hardware : ODROIDC
Revision : 000a
Serial : 1b00000000000000
MEM
# cat /proc/meminfo
MemTotal: 995480 kB
MemFree: 696624 kB
Buffers: 31200 kB
Cached: 119288 kB
SwapCached: 0 kB
Active: 73836 kB
Inactive: 87144 kB
Active(anon): 10596 kB
Inactive(anon): 1572 kB
Active(file): 63240 kB
Inactive(file): 85572 kB
Unevictable: 0 kB
Mlocked: 0 kB
HighTotal: 268288 kB
HighFree: 166504 kB
LowTotal: 727192 kB
LowFree: 530120 kB
SwapTotal: 1049084 kB
SwapFree: 1049084 kB
Dirty: 16 kB
Writeback: 0 kB
AnonPages: 10448 kB
Mapped: 17384 kB
Shmem: 1676 kB
Slab: 58992 kB
SReclaimable: 37252 kB
SUnreclaim: 21740 kB
KernelStack: 1080 kB
PageTables: 516 kB
NFS_Unstable: 0 kB
Bounce: 0 kB
WritebackTmp: 0 kB
CommitLimit: 1546824 kB
Committed_AS: 30284 kB
VmallocTotal: 245760 kB
VmallocUsed: 19892 kB
VmallocChunk: 214012 kB