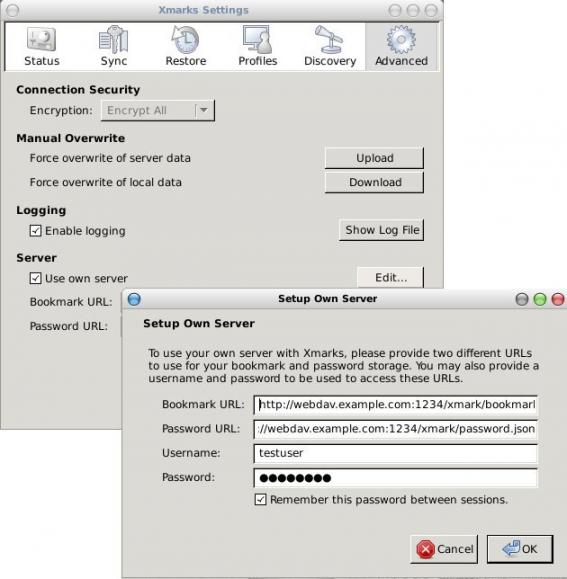
How to setup a custom (webdav) server for xmarks.
No rocket science here,
Download PyWebDAV
Build it: python setup.py develop.
Create a custom directory: mkdir -pv /webdavserver/xmark/
Run something like this:
davserver -D /webdavserver/xmark/ -P 1234 -v -H webdav.example.com -u testuser -p 'testuser'
And then just change the xmark settings to use a custom server:
Remember you should type files and not directories:
http://webdav.example.com:1234/xmark/bookmark.json
http://webdav.example.com:1234/xmark/password.json
If you have problems with suspending your linux box when you are closing lid,
then you should take a quick look on this post !
edit this file: /etc/acpi/handler.sh
vim +/lid /etc/acpi/handler.sh
if you see the lid section empty, then add something like this: pm-suspend
eg.
button/lid)
#echo “LID switched!”>/dev/tty5
pm-suspend
;;
Just to be safe, restart acpi daemon
sudo /etc/rc.d/acpid restart
Thats it !
When a linux box came from hibernation usually resume everything from the previous state.
That means that if someone just hit the power button on your system, in a few minutes he/she will have access to your linux partition and most certain to an already logged-in system !
In a previous post i wrote how to enable Lock Screen after hibernation, but lets face it. This isnt a secure way!
And if someone has access to your hard drive he/she can somehow retrieve your data from your hibernate snapshot.
An alternative and most secure way is to encrypt your hibernate snapshot and then access it through a pass phrase.
First of all, your have to create the key for the encryption process.
Just type: suspend-keygen and then choose the length of the key. I prefer 4096 bits.
After that, you should type a secure pass phrase. Finally choose the name of the key.
A full example:
$ suspend-keygen libgcrypt version: 1.4.6 Key bits (between 1024 and 4096 inclusive) [1024]: 4096 Generating 4096-bit RSA keys. Please wait. Testing the private key. Please wait. Passphrase please (must be non-empty): Confirm passphrase: File name [suspend.key]:
Τransfer your suspend.key to /etc
mv suspend.key /etc/
Now you must edit the below two lines on: /etc/suspend.conf
encrypt = y
RSA key file = /etc/suspend.key
Thats it !
The next time you resume your system from hibernation, you have to write your pass phrase to resume your encrypted hibernate snapshot.
Security is like an onion, it has many many layers.
(and sometimes we end up crying)
For preventing someone to boot your linux (or not) partition it is best to protect your grub menu.
There are two ways:
1st : To use a global password for grub
2nd: To use different passwords for every menu title.
I prefer the second method cause is a more security solution.
We need to create the encrypted password, from our terminal we type:
$ grub-md5-crypt
Password:
Retype password:
$1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
For our example i typed: test
And finally we add the bellow line in /boot/grub/menu.lst
password --md5 $1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
eg.
title Arch Linux [vmlinuz26]
root (hd0,0)
kernel /boot/vmlinuz26 root=/dev/sda1 ro
initrd /boot/kernel26.img
password –md5 $1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
In august i wrote a post about hibernation on linux, Linux hibernation in just 4 steps.
If you want to add screen lock support in resume, you have to create a custom script.
Hibernation’s scripts run in reverse numeric order, so you have to use 00 (double zeros) in the name of your custom script, telling resume process to lock screen at the end.
In my case, i wrote a super simply bash script to slock my screen. I am the only user of my laptop so the bash script is extremely dammy and does only one thing, take a look:
/usr/lib/pm-utils/sleep.d/00lock
#!/bin/bash case $1 in hibernate) # not required. su ebal -c slock & ;; suspend) # not required. ;; thaw) # not required. ;; resume) # not required. ;; *) exit $NA ;; esac
You should replace ebal with your user name and slock with your screen lock program.
Alternative commands against slock are:
- xscreensaver-command –lock
- gnome-screensaver-command ––lock
- xlock
pirsyncd stands for: Python Inotify Rsync Daemon.
Description:
This is an attempt of writing a daemon to watch a directory for kernel’s inotify events and then execute an rsync command to synchronize two different directories (local or remote). This is a poor man’s mirroring or an alternative (not so) real data replication mechanism and it is based on Pyinotify.
From ChangeLog:
- Pyinotify has been updated in version 0.9.0 (20100604)
- Rsync option “–safe-links” has been added
- Scoring 7.38 with pylint (better code styling)
plz try ./pirsyncd –help & ./pirsyncd –examples to see more.
Get the latest version of pirsyncd v20100907
Today i’ve tried the four (4) tiling applications on Xfce, that wikipedia refers as “Third party tiling applications on Xorg”
The winner is: Stiler
Both Tile & QuickTile had a really bad tiling appearance and PyTyle doesnt work with Xfce
For the past year i am looking for http 404 (not found) on my blog. I have only two sites, a blog & a wiki, so without any other web application, i can monitor for web vulnerabilities (that hackers are looking for) by just looking for 404 (Not Found) http errors.
I am using mod_rewrite for URL manipulation. My custom .htaccess redirects every Not Found (404) page to my index.php.
You can use it too, but you must be extremely careful.
You MUST NOT have any valid URLs with one the files below.
If you have, just remove the specific line from the .htaccess file.
An example:
Url: http://balaskas.gr/README doesnt exist,
so if you click on it, you should redirect to my home page.
RewriteEngine on
RewriteRule xmlrpc.php$ index.php
RewriteRule login_page.php$ index.php
RewriteRule setup.php$ index.php
RewriteRule config.inc.php$ index.php
RewriteRule multithumb.php$ index.php
RewriteRule orderSuccess.inc.php$ index.php
RewriteRule send_reminders.php$ index.php
RewriteRule config.php$ index.php
RewriteRule ask_password.php$ index.php
RewriteRule msgimport$ index.php
RewriteRule README$ index.php
RewriteRule fastenv$ index.php
RewriteRule main.php$ index.php
RewriteRule sql.php$ index.php
RewriteRule error.php$ index.php
RewriteRule errors.php$ index.php
RewriteRule sitemap.xml$ index.php
RewriteRule show_image_in_imgtag.php$ index.php
RewriteRule phpmyadmin$ index.php
RewriteRule blackhat.dll$ index.php
RewriteRule general.js$ index.php
RewriteRule get_reminders.php$ index.php
RewriteRule install.txt$ index.php
RewriteRule get_events.php$ index.php
RewriteRule auth.inc.php$ index.php
RewriteRule delete.php$ index.php
RewriteRule adxmlrpc$ index.php
RewriteRule class.dashboard_lms.php$ index.php
RewriteRule home$ index.php
RewriteRule default.php$ index.php
RewriteRule index.inc.php$ index.php
RewriteRule logging.php$ index.php
RewriteRule public.php$ index.php
RewriteRule index.inc.php$ index.php
RewriteRule add-cats.php$ index.php
RewriteRule nosuichfile.php$ index.php
RewriteRule judge.php$ index.php
RewriteRule apple-touch-icon.png$ index.php
RewriteRule apple-touch-icon-precomposed.png$ index.php
RewriteRule host-meta$ index.php
(για πιο τεχνικά, προσπεράστε τον πρόλογο)
Πρόλογος:
Πριν από λίγες μέρες, ανάρτησα το εξής post: 3g on linux, cosmote on the go.
Περιέγραψα, σε απλά βήματα, την διαδικασία σύνδεσης στο διαδίκτυο μέσω ενός usb 3g stick. είχα κατά νου γενικές οδηγίες που θα μπορεί να χρησιμοποιήσει μέχρι και ο πιο απλός χρήστης για να συνδεθεί εύκολα και γρήγορα.
Από τα σχόλια του Post, καλύφθηκαν ακόμα περισσότερα θέματα, κι όχι μόνο τεχνικά. Έγιναν αναφορές για διαφορετικές προσεγγίσεις, γραφικά προγράμματα, σύνδεση μέσω τρίτων προγραμμάτων κι άλλα πολλά.
Θα ήθελα να ευχαριστήσω όλους του φίλους για την συνεισφορά τους, τόσο για τα σχόλιά τους, όσο και για τα ηλεκτρονικά τους μηνύματα.
Με αφορμή το post, τα σχόλια και κάποια από τα ηλεκτρονικά μηνύματα που δέχθηκα, θεώρησα φρόνιμο να δημιουργήσω μία νέα σελίδα, στην οποία θα προσπαθήσω να εξηγήσω όσο πιο απλά μπορώ (κι όχι όσο το δυνατό καλύτερα) όλα όσα είναι απαραίτητα γύρω από το 3G σε διανομές Linux.
Θα είναι μεγάλη μου χαρά να το διαβάσετε (κι αυτό), να το σχολιάσετε (μέσω email) και να με διορθώσετε όπου έχω κάνει λάθος ή έχω παραλείψει κάτι.
You all know: Teenage Mutant Ninja Turtles
Ok, take a look here:
And then here:

See the resemblance?
Just to get serious for a moment, the true story is here:
Gnome History
Απλά, όμορφα και ωραία. 10 λεπτά απομένουν μέχρι να έχετε το 3g έτοιμο στο linux-άκι σας.
Βήμα 1ο:
Η παρακάτω εντολή είναι για το Archlinux, προσαρμόστε την ανάλογα (δλδ εγκαταστήστε ArchLinux):
sudo pacman -S ppp usb_modeswitchΒήμα 2ο:
Βάλτε το usb στον υπολογιστή/laptop σας.
Είναι σχεδόν σίγουρο, ότι θα το δει σαν block device (cd ή δίσκο).
Πληκτρολογήστε την εντολή: dmesg για να δείτε παραπάνω πληροφορίες.
Με την εντολή lsusb θα βρείτε το vendor και product id
Δείτε το αποτέλεσμα της δικής μου εντολής:
Bus 001 Device 004: ID 1bbb:f000 T & A Mobile Phones
Vendor ID: 1bbb ή καλύτερα 0×1bbb
Product ID: f000 ή καλύτερα 0xf000
Βήμα 3ο:
Τώρα πρέπει να μετατρέψουμε το usb-stick από block device σε modem (serial) device.
Πριν προχωρήσετε όμως, επιβεβαιώστε με την εντολή
ls -l /dev/tty* | grep -i usbη διανομή σας, δεν το έχει ήδη κάνει (μπορεί hackers να το έχουν ήδη φτιάξει!)
Εάν δεν φέρει αποτελέσματα, τότε πληκτρολογήστε την εξής εντολή:
sudo usb_modeswitch -W -v 0x1bbb -p 0xf000 -V 0x1bbb -P 0xf000Βήμα 4ο:
Αφαιρέστε το usb-stick, μετρήστε μέχρι το 10 δυνατά (ναι - ναι πρέπει να μετρήσετε δυνατά) και ξανα-βάλτε το στον υπολογιστή/laptop σας.
Τώρα με την εξής εντολή:
ls -l /dev/tty* | grep -i usbθα πρέπει να δείτε τις νέες συσκευές!
Βήμα 5ο:
Τώρα μένει απλά να ρυθμίσετε το ppp.
Πως γίνεται αυτό ρωτάτε; Όπως όλα τα πράγματα στο linux, εύκολα !
Δύο αρχεία πρέπει να δημιουργήσετε:
0001 : /etc/ppp/peers/cosmote
με περιεχόμενο το εξής:
connect “/usr/sbin/chat -v -f /etc/ppp/cosmote.chat”
noipdefault
defaultroute
/dev/gsmmodem
460800
noauth
debug
novj
usepeerdns
nodeflate
nobsdcomp
Μεγάλη προσοχή στην 4η γραμμή που περιγράφει το device (σε εμένα είναι το /dev/ttyUSB2)
0010 : Και τώρα είμαστε έτοιμοι, να δημιουργήσουμε το 2ο αρχείο μας: /etc/ppp/cosmote.chat
ABORT BUSY
ABORT ERROR
REPORT CONNECT
TIMEOUT 10
‘’ AT
OK AT+CGDCONT=16,”IP”,”internet”
OK ATDT*99#
Βήμα 6ο:
Εάν έχετε φτάσει μέχρι εδώ, θα αναρωτιέστε ” Είναι δυνατόν να είναι τόσο μα τόσο απλά τα πράγματα στο linux ? “
Μα ΝΑΙ, είναι τόσο απλά κι εύκολα.
Και μάλιστα είστε σε θέση να περιηγηθείτε στο internet.
Αρκεί να πληκτρολογήστε την εξής εντολή:
sudo pon cosmoteΚι ανοίξτε τον αγαπημένο σας περιηγητή διαδικτύου (εννοείτε ότι μιλάμε για τον midori
Κι όταν θέλετε να σταματήσετε το 3g:
sudo poff cosmoteSome time ago, i wrote a
post in greek of how easy is to use hibernation on linux desktops.
For some time now, i didnt use hibernation and in between i upgrade my laptop a lot of times.
For some strange reason the previous tested (kernel) solution didnt work perfectly.
So i just implement the second hibernation solution: uswsusp
This method provides a userspace suspend program that uses a lot of
scripts to hook your running modules, programs and memory data to a swap partition.
Simple as that in theory, i did small changes on my laptop.
- Installation
sudo pacman -S uswsusp- Kernel HOOKS
Change the resume kernel hook from /etc/mkinitcpio.conf
to uresume (userspace resume)
HOOKS=”base udev autodetect pata scsi sata uresume filesystems”
Save the above file and then run this command:
mkinitcpio -p kernel26- Configuration
Edit /etc/suspend.conf, so that the resume device is linking to your swap partition:
resume device = /dev/sda2
sda2 is my swap partition, just add your swap partition!
- Hibernate
sudo pm-hibernationPS: I read in a lot of HowTos that you have to edit /boot/grub/menu.lst
to add resume path of swap partition, but believe me, thats not necessary!
Κατάγομαι από το χωριό: Καρυές Ανατολικού Ζαγορίου, Ιωαννίνων.
460Khm λοιπόν μακριά από τον τόπο διαμονής μου, και περί τις 5 1/2 ώρες με το αμάξι (χωρίς στάσεις), αποτελεί έναν μακρινό τόπο για διακοπές. Παρόλα αυτά, όποτε βρίσκω χρόνο και μέρες από την δουλειά, προσπαθώ να έρχομαι.
Με πολύ μεγάλη μου έκπληξη (και ευχαρίστηση ταυτόχρονα) διαπίστωσα ότι στο χωριό, υπάρχει open-mesh εξοπλισμός και δίκτυο από το Πανεπιστήμιο Ιωαννίνων !!!
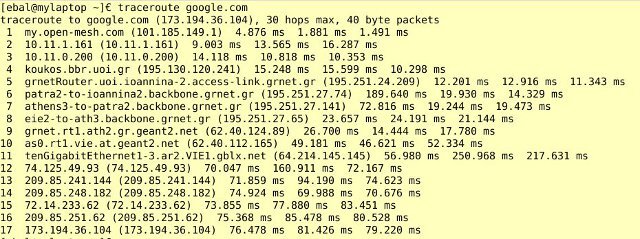
Μάλιστα οι ταχύτητες που πιάνω από το σπίτι μου (50%), κι όχι από την κεντρική πλατεία του χωριού (στην οποία είναι στημένος ο κόμβος), είναι καλύτερες κι από αυτές στην Αθήνα!
Ένας από τους άθλους για έναν νέο χρήστη (καλά όχι μόνο για τους νέους χρήστες) στο linux, είναι η απομνημόνευση όλων αυτών των καταλόγων. Τι είναι όλοι αυτοί οι κατάλογοι και τι σημαίνουν;
Η λύση είναι φυσικά να ρίξουμε μια ματιά στο εξής link:
Filesystem Hierarchy Standard
Αλλά διαβάζοντας το Linux Gazette , έμαθα για την εξής εντολή:
man hier
Είναι ένας πολύ χρήσιμος τρόπος να βρει κανείς εύκολα τι σημαίνουν όλοι αυτοί οι κατάλογοι, χωρίς να χρειαστεί να ανοίξει internet!
On January i wrote a personal script to keep my package list and latest conf files on a backup-snapshot mechanism: abs4snap . Page on wiki: abs4snap for archlinux.
Today i wanted to delete some libraries from /usr/lib/ folder path!
And i did a little mistake :(
I wanted to write:
rm -f /usr/lib/libjsp*
but i wrote:
rm -f /usr/lib/lib*
Simple as that my distro (archlinux) becomes a jigsaw puzzles !
Just pieces here and there !
What the f@#$% i could do to save my distro ?
I am using archlinux, so my package manager is: pacman, but pacman uses libraries from /usr/lib folder path !
The solution was to reinstall my distro of course.
Or there is another way ?
A couple days before, i wrote a post how to build a static binary with: statifier. So i had my pacman package list and a pacman static binary file !
The solution was in front of me.
awk '{print "pacman-static -S --noconfirm " $1}' package-list | sh And with in a few minutes my distro and /usr/lib was in perfect mode again !!!
So remember:
BACKUP your data.
A nice (but not perfect) tool to create a static package is: statifier
Here is a simple but useful mini how to:
(as root)
# echo -n 0 > /proc/sys/kernel/randomize_va_space
# ldd /usr/bin/pacman
linux-gate.so.1 => (0xb7fe1000)
libalpm.so.5 => /usr/lib/libalpm.so.5 (0xb7fa8000)
libc.so.6 => /lib/libc.so.6 (0xb7e5d000)
libfetch.so => /usr/lib/libfetch.so (0xb7e4f000)
libarchive.so.2 => /usr/lib/libarchive.so.2 (0xb7e0f000)
/lib/ld-linux.so.2 (0xb7fe2000)
libssl.so.1.0.0 => /usr/lib/libssl.so.1.0.0 (0xb7dbd000)
libcrypto.so.1.0.0 => /usr/lib/libcrypto.so.1.0.0 (0xb7c43000)
libacl.so.1 => /lib/libacl.so.1 (0xb7c3c000)
libattr.so.1 => /lib/libattr.so.1 (0xb7c37000)
libexpat.so.1 => /usr/lib/libexpat.so.1 (0xb7c11000)
liblzma.so.0 => /usr/lib/liblzma.so.0 (0xb7bef000)
libbz2.so.1.0 => /lib/libbz2.so.1.0 (0xb7bde000)
libz.so.1 => /usr/lib/libz.so.1 (0xb7bc9000)
libdl.so.2 => /lib/libdl.so.2 (0xb7bc5000)
libpthread.so.0 => /lib/libpthread.so.0 (0xb7bab000)
# statifier /usr/bin/pacman /tmp/pacman.static-3.4.0
# ldd /tmp/pacman.static-3.4.0
not a dynamic executable
# ls -l /usr/bin/pacman /tmp/pacman.static-3.4.0
-rwxr-xr-x 1 root root 4530176 2010-07-30 20:47 /tmp/pacman.static-3.4.0
-rwxr-xr-x 1 root root 70708 2010-06-21 15:54 /usr/bin/pacman