ACME v2 and Wildcard Certificate Support is Live
We have some good news, letsencrypt support wildcard certificates! For more details click here.
The key phrase on the post is this:
Certbot has ACME v2 support since Version 0.22.0.
unfortunately -at this momment- using certbot on a centos6 is not so trivial, so here is an alternative approach using:
acme.sh
acme.sh is a pure Unix shell script implementing ACME client protocol.
# curl -LO https://github.com/Neilpang/acme.sh/archive/2.7.7.tar.gz
# tar xf 2.7.7.tar.gz# cd acme.sh-2.7.7/
[acme.sh-2.7.7]# ./acme.sh --version
https://github.com/Neilpang/acme.sh
v2.7.7PowerDNS
I have my own Authoritative Na,e Server based on powerdns software.
PowerDNS has an API for direct control, also a built-in web server for statistics.
To enable these features make the appropriate changes to pdns.conf
api=yes
api-key=0123456789ABCDEF
webserver-port=8081and restart your pdns service.
To read more about these capabilities, click here: Built-in Webserver and HTTP API
testing the API:
# curl -s -H 'X-API-Key: 0123456789ABCDEF' http://127.0.0.1:8081/api/v1/servers/localhost | jq .
{
"zones_url": "/api/v1/servers/localhost/zones{/zone}",
"version": "4.1.1",
"url": "/api/v1/servers/localhost",
"type": "Server",
"id": "localhost",
"daemon_type": "authoritative",
"config_url": "/api/v1/servers/localhost/config{/config_setting}"
}Enviroment
export PDNS_Url="http://127.0.0.1:8081"
export PDNS_ServerId="localhost"
export PDNS_Token="0123456789ABCDEF"
export PDNS_Ttl=60
Prepare Destination
I want to save the certificates under /etc/letsencrypt directory.
By default, acme.sh will save certificate files under /root/.acme.sh/balaskas.gr/ path.
I use selinux and I want to save them under /etc and on similar directory as before, so:
# mkdir -pv /etc/letsencrypt/acme.sh/balaskas.gr/
Create WildCard Certificate
Run:
# ./acme.sh
--issue
--dns dns_pdns
--dnssleep 30
-f
-d balaskas.gr
-d *.balaskas.gr
--cert-file /etc/letsencrypt/acme.sh/balaskas.gr/cert.pem
--key-file /etc/letsencrypt/acme.sh/balaskas.gr/privkey.pem
--ca-file /etc/letsencrypt/acme.sh/balaskas.gr/ca.pem
--fullchain-file /etc/letsencrypt/acme.sh/balaskas.gr/fullchain.pemHSTS
Using HTTP Strict Transport Security means that the browsers probably already know that you are using a single certificate for your domains. So, you need to add every domain in your wildcard certificate.
Web Server
Change your VirtualHost
from something like this:
SSLCertificateFile /etc/letsencrypt/live/balaskas.gr/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/balaskas.gr/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateChainFile /etc/letsencrypt/live/balaskas.gr/chain.pemto something like this:
SSLCertificateFile /etc/letsencrypt/acme.sh/balaskas.gr/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/acme.sh/balaskas.gr/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateChainFile /etc/letsencrypt/acme.sh/balaskas.gr/fullchain.pemand restart your web server.
Browser
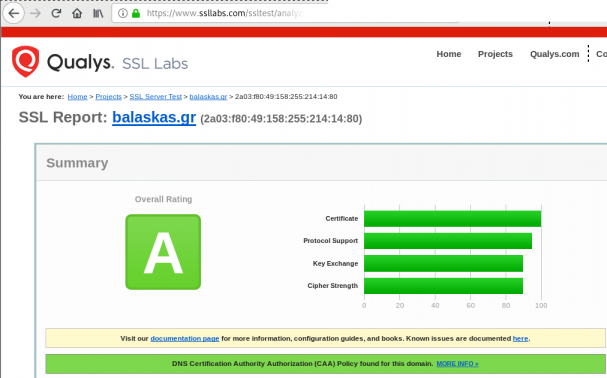
Quallys
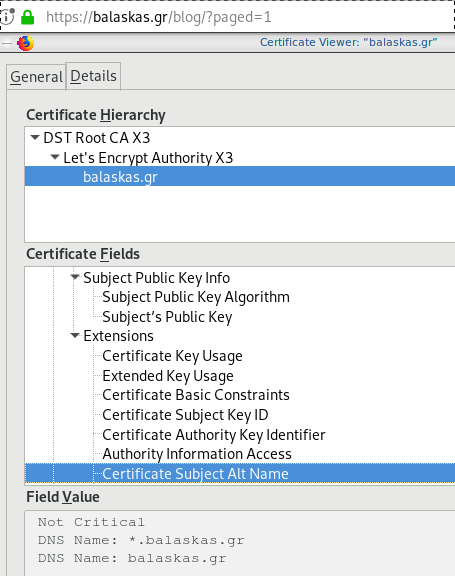
Validation
X509v3 Subject Alternative Name
# openssl x509 -text -in /etc/letsencrypt/acme.sh/balaskas.gr/cert.pem | egrep balaskas
Subject: CN=balaskas.gr
DNS:*.balaskas.gr, DNS:balaskas.gr