Yes and no …
The swap partition is an extended memory. Newest kernels are reserving the entire ram at start so when an application needs more ram, swap partition is here for us. But what if our swap partition is full ? That cannot be done cause there is a percent that kernel is using for the swap partition. This kernel value is described here:
cat /proc/sys/vm/swappiness
In most linux systems the default value is 60 percent.
In virtual machines we should reduce this percent to something small cause of IO limitations.
In our desktops we can increase it, to even higher values.
But what if we need more ram, more swap ?
What if our applications are running all together and the swap partition is in its limits ?
Then just … swapoff !!!
With swapoff the system will drop the swap partition!
But how this is more helpful ?
It isnt !
swapoff frees up unused memory and we can change the value of swappiness to something higher, lets say:
sudo sysctl -w vm.swappiness=80
And then swapon the swap partition again …
If we need to make a permanent change for the swappiness, we need to make it to /etc/sysctl.conf
Φρικτή εμπειρία μου!
Γράφω αυτό με δάκρυα στα μάτια μου, ήρθα εδώ κάτω στο Λονδίνο, Ηνωμένο Βασίλειο
για ολιγοήμερες διακοπές, δυστυχώς, ήμουν θύμα ληστείας στο πάρκο στο δρόμο μου
προς το ξενοδοχείο όπου έμεινε, όλα τα μετρητά, πιστωτική κάρτα και κυττάρων
κλάπηκαν από εμένα αλλά ευτυχώς για μένα που έχω ακόμα διαβατήρια μαζί μου.
Έχω την πρεσβεία και την Αστυνομία εδώ αλλά δεν είναι συμβάλλοντας σε όλα τα
ζητήματα και η πτήση μου φεύγει σε λίγες ώρες, αλλά είμαι έχοντας προβλήματα
διευθέτηση των λογαριασμών του ξενοδοχείου και ο διευθυντής του ξενοδοχείου δεν
θα με άφηνε να φύγω μέχρι να διευθετήσει τους λογαριασμούς.
Είμαι φρίκαρε στο moment.I χρειάζονται επείγουσα βοήθεια.
You can find my presentation on Athens Digital Week 2010 here: How to Contribute to Open Source Projects or to Communities
I am using a socks proxy on my office. This of course isnt a bug but a feature!
I want to mount a remote folder on a server outside my office dmz over ssh. So i ‘ve looked up for ssfs that mount an ssh remote folder with fuse (userspace). The main problem is that sshfs doesnt support any proxy settings! Thats a bummer.
So is there a way ?
From the command line i can pass sshfs through proxychains. But how can i do this through fstab ?
The normal entry on fstab is something like this:
sshfs#username@example.com:/home/username/folder/ /home/username/remote/folder/ fuse user,reconnect,compression=yes,ssh_protocol=2 0 0
and from cli is something like this:
proxychains sshfs username@example.com:/home/username/folder/ /home/username/remote/folder/ -C -o reconnect,ssh_protocol=2
That problem gave me a morning headache and i postponed everything i should be doing till i solved it.
And i solved it !!!
I didnt know that the first column in /etc/fstab can be a program or a shell script.
Do you ?
I learned it today, and i am extremely happy to learn linux stuffs with the old transitional way:
try & error.
So the above headache resolved by this entry on fstab:
proxysshfs /home/username/remote/folder/ fuse user,noauto 0 0
and this script: /usr/local/bin/proxysshfs
#!/bin/bash
unset http_proxy ; unset https_proxy ;
proxychains sshfs username@example.com:/home/username/folder/ /home/username/remote/folder/ -C -o reconnect,ssh_protocol=2
So now, everytime i am writing something like this:
mount /home/username/remote/folder/
my proxysshfs script is set in motion and the result is to execute the above command and finally mount the remote folder over ssh through a proxy.
How to protect your grub menu with password
Not so far ago, i wrote a post about adding password to grub.
I have to be complete honest with you: “I was wrong !”
I found the next day why i was wrong, but i was too ashamed to errata my own post!
So lets start again from the begging.
In the previous post i had added successful a password on my linux entry on grub menu. But that didnt mean anything, cause anybody can edit the grub menu at boot time and remove the password entry ! Yes its simply as that!
You have to add a lock entry on grub menu.
After a lot of tests i think i found the “correct” way of securing my grub menu.
Removing password from any menu title and add only a global password for grub with lock mechanism.
So we need to create the encrypted password, from our terminal we type:
$ grub-md5-crypt
Password:
Retype password:
$1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
For our example i typed: test
And finally (finally) my /boot/grub/menu.lst looks like this:
password –md5 $1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
title Arch Linux
root (hd0,0)
kernel /boot/vmlinuz26 root=/dev/sda1 ro
initrd /boot/kernel26.img
lock
I’ve just uploaded some photos from FrOSCamp 2010 and FUDCon:Zurich 2010 here:
ETH have already uploaded the video recordings here: FrOSCamp Talks 2010
I’ve just added 6 beers in my flickr BEER set!
- St.Galler Klosterbräu
- Free Beer
- Schützengarten Weisserbier Engel
- St.Galler Klosterbräu Schützengarten
- Cardinal draft
- Budweiser Budvar, Czech Imported Lager
Take a look:Flickr BEER Set
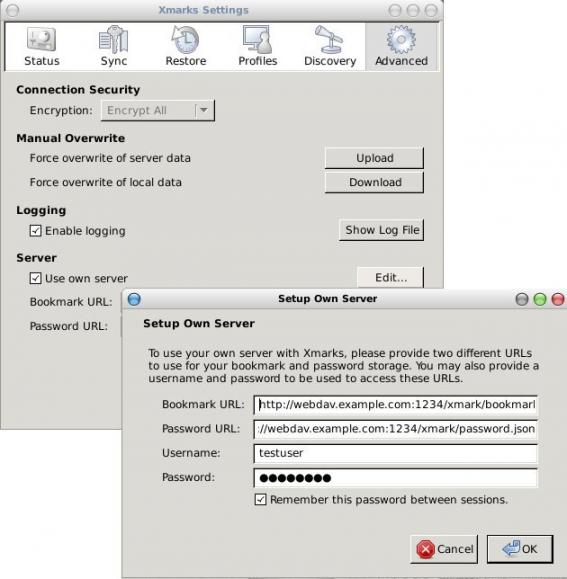
How to setup a custom (webdav) server for xmarks.
No rocket science here,
Download PyWebDAV
Build it: python setup.py develop.
Create a custom directory: mkdir -pv /webdavserver/xmark/
Run something like this:
davserver -D /webdavserver/xmark/ -P 1234 -v -H webdav.example.com -u testuser -p 'testuser'
And then just change the xmark settings to use a custom server:
Remember you should type files and not directories:
http://webdav.example.com:1234/xmark/bookmark.json
http://webdav.example.com:1234/xmark/password.json
Μην γελιόμαστε, σίγουρα ΟΧΙ.
Σημαίνει ότι χρειάζεται ακόμα πάρα πολύ δουλειά, ώστε κάποια στιγμή να επιτύχεις.
Οπότε: Gotta Keep Reading
Πάντα αφήνω τους άλλους … να κλείνουν τα ταξίδια μου.
Αεροπορικά-ξενοδοχεία-εισιτήρια!
Εγώ το μόνο που κάνω κάθε φορά είναι να πληρώνω ότι μου αντιστοιχεί.
Δυστυχώς για Ρώμη, έγινε κάπως έτσι … και δυστυχώς ο έτερος φίλος (εξαιρετικός φίλος, από τους λίγους που εκτιμώ τόσο πολύ) έμεινε περισσότερο στα σχόλια του booking.com για να αποφασίσουμε για ξενοδοχείο.
Έτσι λοιπόν καταλήξαμε σε ένα ξενοδοχείο …. στην μέση του πουθενά, με μοναδική συγκοινωνία ένα και μόνο λεωφορείο, ανά μισάωρο (ο καίσαρας να το κάνει μισάωρο)! Και περίπου μία ώρα μακριά από το κέντρο!
Μετά την καθυστέρηση της easy jet (σε ευχαριστώ easy jet, για ακόμα μία φορά), και περίπου μιάμιση ώρα (το λιγότερο - μπορεί να ήταν και κοντά δύο) φτάσαμε στο ξενοδοχείο! Δυστυχώς είναι και non refundable !
Έτσι λοιπόν … η εμπιστοσύνη στο internet, η πίστη στους φίλους, αυτή την φορά είχαν ως αποτέλεσμα να τρώω … στο δρόμο από καντίνα μαζί με μισή ντουζίνα ινδούς, παραδίπλα από κάποιες ιερόδουλες που ξεκίνησαν την βραδινή τους εργασία.
ΔΕΝ προτείνετε (με την καμία όμως - μακριά όλοι): http://www.hotelromulus.com/
κι ορίστε η φώτο για απόδειξη:
ΥΓ: Οι άσπροι είμαστε οι έλληνες (για όσους δεν το έπιασαν)
If you have problems with suspending your linux box when you are closing lid,
then you should take a quick look on this post !
edit this file: /etc/acpi/handler.sh
vim +/lid /etc/acpi/handler.sh
if you see the lid section empty, then add something like this: pm-suspend
eg.
button/lid)
#echo “LID switched!”>/dev/tty5
pm-suspend
;;
Just to be safe, restart acpi daemon
sudo /etc/rc.d/acpid restart
Thats it !
When a linux box came from hibernation usually resume everything from the previous state.
That means that if someone just hit the power button on your system, in a few minutes he/she will have access to your linux partition and most certain to an already logged-in system !
In a previous post i wrote how to enable Lock Screen after hibernation, but lets face it. This isnt a secure way!
And if someone has access to your hard drive he/she can somehow retrieve your data from your hibernate snapshot.
An alternative and most secure way is to encrypt your hibernate snapshot and then access it through a pass phrase.
First of all, your have to create the key for the encryption process.
Just type: suspend-keygen and then choose the length of the key. I prefer 4096 bits.
After that, you should type a secure pass phrase. Finally choose the name of the key.
A full example:
$ suspend-keygen libgcrypt version: 1.4.6 Key bits (between 1024 and 4096 inclusive) [1024]: 4096 Generating 4096-bit RSA keys. Please wait. Testing the private key. Please wait. Passphrase please (must be non-empty): Confirm passphrase: File name [suspend.key]:
Τransfer your suspend.key to /etc
mv suspend.key /etc/
Now you must edit the below two lines on: /etc/suspend.conf
encrypt = y
RSA key file = /etc/suspend.key
Thats it !
The next time you resume your system from hibernation, you have to write your pass phrase to resume your encrypted hibernate snapshot.
Security is like an onion, it has many many layers.
(and sometimes we end up crying)
For preventing someone to boot your linux (or not) partition it is best to protect your grub menu.
There are two ways:
1st : To use a global password for grub
2nd: To use different passwords for every menu title.
I prefer the second method cause is a more security solution.
We need to create the encrypted password, from our terminal we type:
$ grub-md5-crypt
Password:
Retype password:
$1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
For our example i typed: test
And finally we add the bellow line in /boot/grub/menu.lst
password --md5 $1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
eg.
title Arch Linux [vmlinuz26]
root (hd0,0)
kernel /boot/vmlinuz26 root=/dev/sda1 ro
initrd /boot/kernel26.img
password –md5 $1$nNyIl/$2rdkv9UCclYQu1Hb0hxiQ/
In august i wrote a post about hibernation on linux, Linux hibernation in just 4 steps.
If you want to add screen lock support in resume, you have to create a custom script.
Hibernation’s scripts run in reverse numeric order, so you have to use 00 (double zeros) in the name of your custom script, telling resume process to lock screen at the end.
In my case, i wrote a super simply bash script to slock my screen. I am the only user of my laptop so the bash script is extremely dammy and does only one thing, take a look:
/usr/lib/pm-utils/sleep.d/00lock
#!/bin/bash case $1 in hibernate) # not required. su ebal -c slock & ;; suspend) # not required. ;; thaw) # not required. ;; resume) # not required. ;; *) exit $NA ;; esac
You should replace ebal with your user name and slock with your screen lock program.
Alternative commands against slock are:
- xscreensaver-command –lock
- gnome-screensaver-command ––lock
- xlock
pirsyncd stands for: Python Inotify Rsync Daemon.
Description:
This is an attempt of writing a daemon to watch a directory for kernel’s inotify events and then execute an rsync command to synchronize two different directories (local or remote). This is a poor man’s mirroring or an alternative (not so) real data replication mechanism and it is based on Pyinotify.
From ChangeLog:
- Pyinotify has been updated in version 0.9.0 (20100604)
- Rsync option “–safe-links” has been added
- Scoring 7.38 with pylint (better code styling)
plz try ./pirsyncd –help & ./pirsyncd –examples to see more.
Get the latest version of pirsyncd v20100907
Today i’ve tried the four (4) tiling applications on Xfce, that wikipedia refers as “Third party tiling applications on Xorg”
The winner is: Stiler
Both Tile & QuickTile had a really bad tiling appearance and PyTyle doesnt work with Xfce