Hits : 6638
Last Edit: 01.04.2016 09:48
OpenLDAP :: Notes
Contents
Lightweight Directory Access Protocol
Installation
client, library & server
# yum -y install openldap openldap-clients openldap-servers
Info
# /usr/sbin/slapd -VVV
@(#) $OpenLDAP: slapd 2.4.40 (Nov 10 2015 09:41:16) $
mockbuild@c6b8.bsys.dev.centos.org:/builddir/build/BUILD/
openldap-2.4.40/openldap-2.4.40/build-servers/servers/slapd
Included static backends:
config
ldif
monitor
bdb
hdb
ldap
mdb
meta
null
passwd
relay
shell
sockStatus
[~] # /etc/init.d/slapd status slapd is stopped [~] # /etc/init.d/slapd restart Stopping slapd: [FAILED] Starting slapd: [ OK ] [~] # chkconfig slapd on [~] # netstat -ntulp | grep slapd tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 2690/slapd tcp 0 0 :::389 :::* LISTEN 2690/slapd [~] # iptables -nvL | grep 389 [~] # ]# ps -e fuwww | grep l[d]ap ldap 11986 0.0 0.2 560100 5660 ? Ssl 18:03 0:00 /usr/sbin/slapd -h ldap:/// ldapi:/// -u ldap
Display Entire Config
# ldapsearch -Y EXTERNAL -H ldapi:/// -b "cn=config"
Identify olcDatabase
# ldapsearch -H ldapi:// -Y EXTERNAL -b "cn=config" -LLL -Q "olcDatabase=*" dn
dn: olcDatabase={-1}frontend,cn=config
dn: olcDatabase={0}config,cn=config
dn: olcDatabase={1}monitor,cn=config
dn: olcDatabase={2}hdb,cn=configBe careful if it is hdb or bdb for later configuration
hdb stands for: hierarchical database
Initial Conf
OpenLDAP is based on berkeley DB databases (key: value),
so we need to use a default configuration file for openldap to use with BDB/HDB databases.
# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
Default openldap conf dir
# cd /etc/openldap/slapd.d/
Default ldapsearch
# ldapsearch -LLL -x -h localhost -p 389 -b '' -s base '(&)' namingContexts dn: namingContexts: dc=my-domain,dc=com
or via URI
# ldapsearch -Q -Y EXTERNAL -H ldapi:/// -s base '(&)' namingContexts
# ldapsearch -LLL -x -h localhost -s base dn: objectClass: top objectClass: OpenLDAProotDSE
[~] # ldapsearch SASL/DIGEST-MD5 authentication started Please enter your password: ldap_sasl_interactive_bind_s: Invalid credentials (49) additional info: SASL(-13): user not found: no secret in database [~] # ldapsearch -x # extended LDIF # # LDAPv3 # base <> (default) with scope subtree # filter: (objectclass=*) # requesting: ALL # # search result search: 2 result: 32 No such object # numResponses: 1
Password
Create a new -strong- password:
# slappasswd
New password:
Re-enter new password:
{SSHA}3u4JMk96UgMheppVZpdr7HmMJFKHRpEdDomain Component
The Wrong Way
bdb.ldif
# vim "/etc/openldap/slapd.d/cn=config/olcDatabase={2}bdb.ldif"diff
-olcSuffix: dc=my-domain,dc=com
+olcSuffix: dc=example,dc=org
-olcRootDN: cn=Manager,dc=my-domain,dc=com
+olcRootDN: cn=Manager,dc=example,dc=org
+olcRootPW: {SSHA}44qvcGE22p2qwgbTH49PNRZjjRs6PIZ4monitor.ldif
# vim "/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif"diff
- nal,cn=auth" read by dn.base="cn=manager,dc=my-domain,dc=com" read by * n + nal,cn=auth" read by dn.base="cn=manager,dc=example,dc=org" read by * n
The Correct Way
# cat openldap_initial.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=admin,dc=example,dc=org" read by * none
dn: olcDatabase={2}bdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=example,dc=org
-
replace: olcRootDN
olcRootDN: cn=admin,dc=example,dc=org
-
add: olcRootPW
olcRootPW: {SSHA}3u4JMk96UgMheppVZpdr7HmMJFKHRpEdand then just use ldap modify
# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f /root/openldap_initial.ldif
test it:
# ldapsearch -LLLL -Q -Y EXTERNAL -H ldapi:/// -s base '(&)' namingContexts dn: namingContexts: dc=example,dc=org
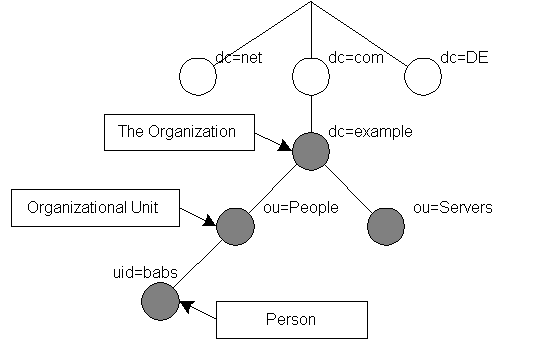
Directory Information Tree
organizationalUnit
# example.gr dn: dc=example,dc=org dc: example objectClass: dcObject objectClass: organizationalUnit ou: example.gr
Domain / Groups / People
# Domains dn: ou=Domains,dc=example,dc=org objectClass: organizationalUnit ou: Domains # Users dn: ou=People,dc=example,dc=org objectClass: organizationalUnit ou: People # Groups dn: ou=Groups,dc=example,dc=org objectClass: organizationalUnit ou: Groups
Create a new Domain
# New Domain dn: dc=example.gr,ou=Domains,dc=example,dc=org dc: example.gr objectclass: dNSDomain objectclass: top
Create a new User
dn: uid=test,ou=People,dc=example,dc=org objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson objectClass: posixAccount mail: username@example.gr cn: username example sn: example givenName: username uid: test uidNumber: 99 gidNumber: 12 homeDirectory: /Maildir/test userPassword: test
Add the ldif
# ldapmodify -x -W -D cn=Manager,dc=example,dc=org -a -f example.ldif Enter LDAP Password: adding new entry "dc=example,dc=org" adding new entry "ou=Users,dc=example,dc=org" adding new entry "uid=test,ou=Users,dc=example,dc=org" ## # ldapadd -Q -Y EXTERNAL -H ldapi:/// -f /root/openldap_initial.ldif
ldapvi – LDAP client
# /usr/bin/ldapvi --discover --host localhost
CheckPoint
In order to clean up the Berkeley DB log files, you must draw a line in the sand and then use a command to remove the unnecessary log files
Note that the db_checkpoint command must be used first in order for the db_archive command to work.
As root execute the following command to set a checkpoint within Berkeley DB, which will flush all of the active transactions into the DB:
# cd /var/lib/ldap/ # db_checkpoint -1 or # db_checkpoint -1 /var/lib/ldap/
Then, (if you're interested or to verify) run the db_archive command to view which files aren't needed:
# db_archive -a -h /var/lib/ldap/
Now, you can actually remove the log files that are no longer in use:
# db_archive -d -h /var/lib/ldap/
For good measure, restart jabberd and you should be all set.
# /etc/init.d/openldap restart